In one of the largest data breaches ever, Capital One admitted recently that more than 100 million customer records were compromised. It is not particularly surprising that a skilled cybercriminal was once again able to extract what should have been well-protected customer information.
The knee jerk reaction for most enterprises will likely be more frequent pentesting, tightening up vulnerability assessments and adding to the perimeter defense toy chest. All of that is good, but we arrived here for a reason, and this dire situation is not going to correct itself with more of the same.
Lumu has developed a new strategy, and we’re helping businesses shift to a completely new approach, one that flips the premise that your data is secure and instead assumes that you are compromised.
Here are a few of our guiding principles to detect and stop breaches with speed:
- Assume you are compromised. While pentesting and vulnerability assessments are fundamental to any security testing strategy, we’re past the point where they are sufficient. Organizations must embrace the hypothesis that adversaries might already be inside. Doing this exercise once is great and will surely make an impact, not only with anxiety levels but also with post-breach resource and budget planning. Doing it continuously by implementing the concept of continuous compromise detection will become the gold standard and anchor of cyber-resilience in today’s world.
- Unlock the value of your network data to identify compromise at speed. In every attack, adversaries must have access to your network. This means that listening actively and continuously to what your network has to tell you will reveal the compromise level of your organization. The extended definition of the network in today’s world includes on-premises environments, hybrid networks, and roaming devices.
- Streamline the process of data collection to illumination. Easier said than done, and where most enterprises may fall short. It is absolutely critical to capture all relevant data with a process that is simple, timely, reliable and continuous. There will never be a proper assessment for any given incident if you are not capturing all the data. Lumu helps you go from collection to continuous and complete illumination.
The Product
Continuous Compromise Assessment
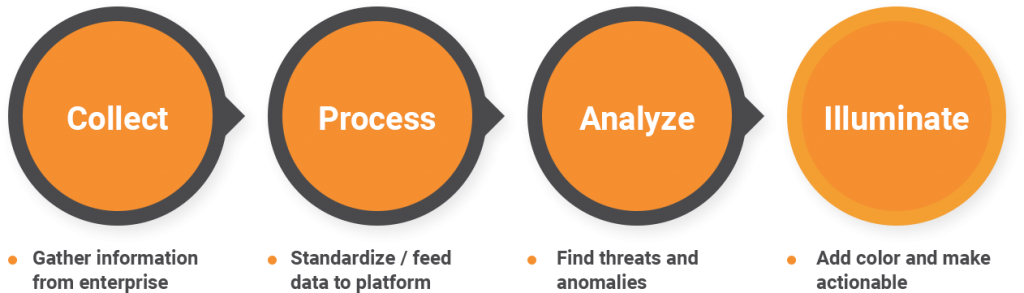
- Make it measurable. Management Thinker Peter Druker has said that “you can’t manage what you can’t measure.” This is as true for management as it is for control theory. Cybersecurity is both a system (a very complex one) and arguably one of the most critical processes in today’s enterprises. Without clear objectives, you’re in a constant state of guessing, and it becomes impossible to adjust the variables of the system (the cyber-defense architecture) to pursue a better output. Lumu helps to implement a factual process to continuously measure the ideal state of a cybersecurity architecture (zero-compromise) and feedback the deviation of that clear objective towards the defense infrastructure. Without this loop, nothing is measurable, and we would never know if we are going in the right direction.
The Era of the Breach Dark Days
Time and time again enterprises are falling like dominoes when it comes to breaches. The overall story is the same: one way or another hackers bypass defenses, gain access and exfiltrate sensitive data. Enterprise security teams are left in the dark during the attack process and remain unaware for months or even years down the road. This has happened, is happening or can happen to any and all enterprises including those with solid pen testing results and $100M+ security budgets.
The odds are against enterprises, which can be targeted with hundreds of thousands of daily attacks. There are so many unique attacks that it is extremely challenging to decide what to prioritize and where to invest. Security teams are inundated with noise and can never seem to answer with certainty if their defenses are indeed working and, most importantly, if their organizations are compromised.
In the meantime, hackers only need to get lucky once. They very well recognize that systems are awfully complex, which means that mistakes are bound to happen. Find one system’s weak spot, and they are in business.
Don’t let your company be the subject of the next set of headlines about new breaches. Don’t fall into the same trap of doing more of the same. This time, dare to be different so that you always know your level of compromise and can stop a breach with speed. Start illuminating your network data today with a Lumu Free account.




