Every asset connected to the network is an open door for cybercriminals. Protecting high-value assets only is known to be highly ineffective. Obtain confirmed compromise visibility across the network including cloud environments, remote devices, IoT, OT, and more—for a holistic view of your compromise level.
“To understand the security of a system, you need to look at the entire system.” Security Guru, Bruce Schneier
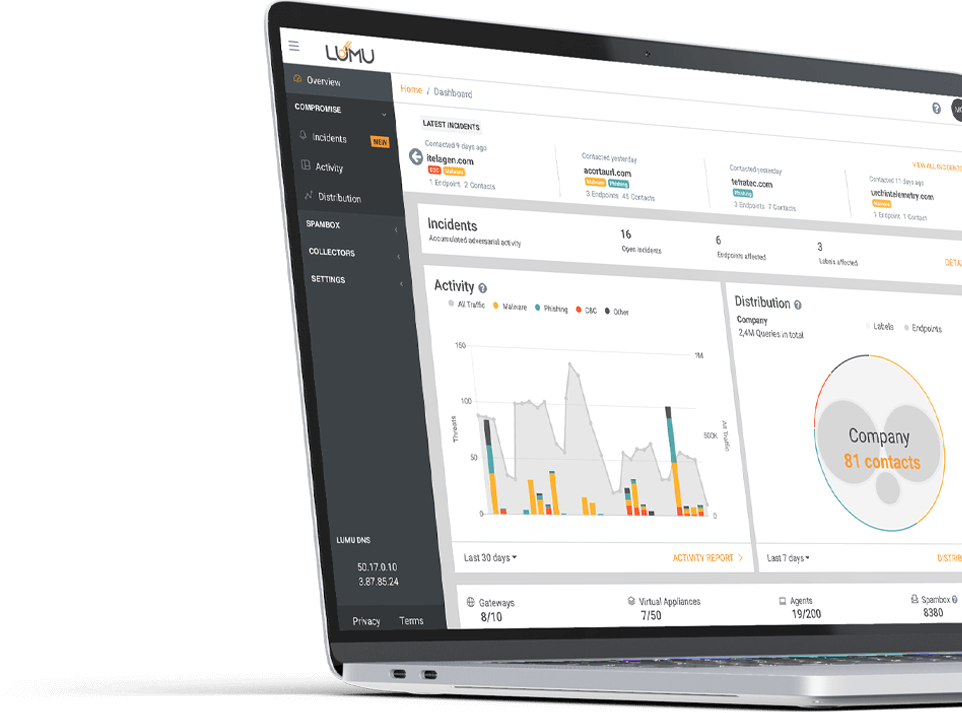
Be reassured that your entire enterprise network is covered by Lumu’s ability to ingest a wide range of metadata including DNS, network flows, proxy and firewall access logs, and spam. All this metadata is analyzed by Lumu’s Illumination process in real time for the best Continuous Compromise Assessment™ available today.
When new IoCs are determined by Lumu’s AI capabilities, you need to know if your network was in contact with those IoCs in the past. Lumu’s Playback feature stores metadata for up to 2 years.

Gain a holistic view of the cybersecurity posture of your organization with real-time confirmed compromise information.
Threat hunters need a baseline from which to make precise hypotheses for testing. Lumu offers factual data on the most important baseline of a cybersecurity system: real-time compromises.
Quickly identify relevant TTPs of interest. Blue teams can tune cyberdefenses according to identified weaknesses, while red teams test defenses against their most relevant TTPs. The entirety of the 200+ TTPs in the MITRE ATT&CK Matrix is automated within the Lumu Portal.
* How To Integrate Threat Intelligence Into Your Security Program by By Brian Kime with Merritt Maxim, Benjamin Corey, Peggy Dostie, Forrester January 15, 2021
Lumu navigates the abundant world of data within your organization, letting teams access conclusive, actionable information in a single tool, allowing for faster, more efficient threat hunting.
“Not using automation to handle many of the low-risk, repeatable tasks like moving data between systems only hampers your threat intelligence efforts.”* - Forrester
Security starts with visibility: you cannot secure what you cannot see. Users connecting from home cannot be blind spots in your compromise visibility. When remote devices return to the office, physically bypassing your perimeter, know that your network is continuously being assessed for evidence of compromise.
94% of CISOs reported that securing their remote workforce was an “absolute priority” - 2021 CISO Priorities Flashcard
With zero impact on your users’ work, Lumu collects remote devices’ metadata for analysis. The Lumu Agent is a lightweight solution built with the reality of remote work in mind
If your workers are connecting via VPN or SDP, Lumu has them covered. We offer the option to integrate with either full-tunnel or split-tunnel configurations.

With Incidents, teams are alerted about single compromises rather than the thousands of contacts they could cause, dramatically reducing alert rates. Lumu groups all related contacts from a particular IoC into one incident. Therefore the simplified view allows teams to manage incidents, track statuses, and review which compromises have been resolved.
Compromise Context does the heavy lifting when investigating alerts. For each detected compromise, Lumu provides additional resources about its nature, including compromise patterns, distribution, playbooks, third-party resources, and more.
Lumu identifies which devices have been compromised in real time, allowing for lightning-fast incident response.
We believe any company can operate cybersecurity proficiently—they just need the right tool. Combat alert fatigue and find peace of mind through actionable incident reporting.
“As much as 25% of a security analyst’s time is spent chasing false positives, before being able to tackle real findings.” Ponemon Institute Exabeam Productivity Report

International financial institution relieves ransomware anxiety and reduces adversaries’ dwell time.

Healthcare provider proactively embraces Continuous Compromise Assessment™, in the wake of sector-wide attacks.

Commercial broadcaster bolsters their defenses with Continuous Compromise Assessment™ to maintain uninterrupted service delivery.

Top-level agency streamlines security efforts and protections to constituents in the wake of globally increasing municipal breaches.

Market-leading retailer improves their cybersecurity posture and unifies compromise intelligence across their widely dispersed, diverse network.
This freely-available cybersecurity ebook represents a curated collection of all the research and whitepapers previously released by Lumu Technologies.

© Lumu Technologies All rights reserved. | Legal information.