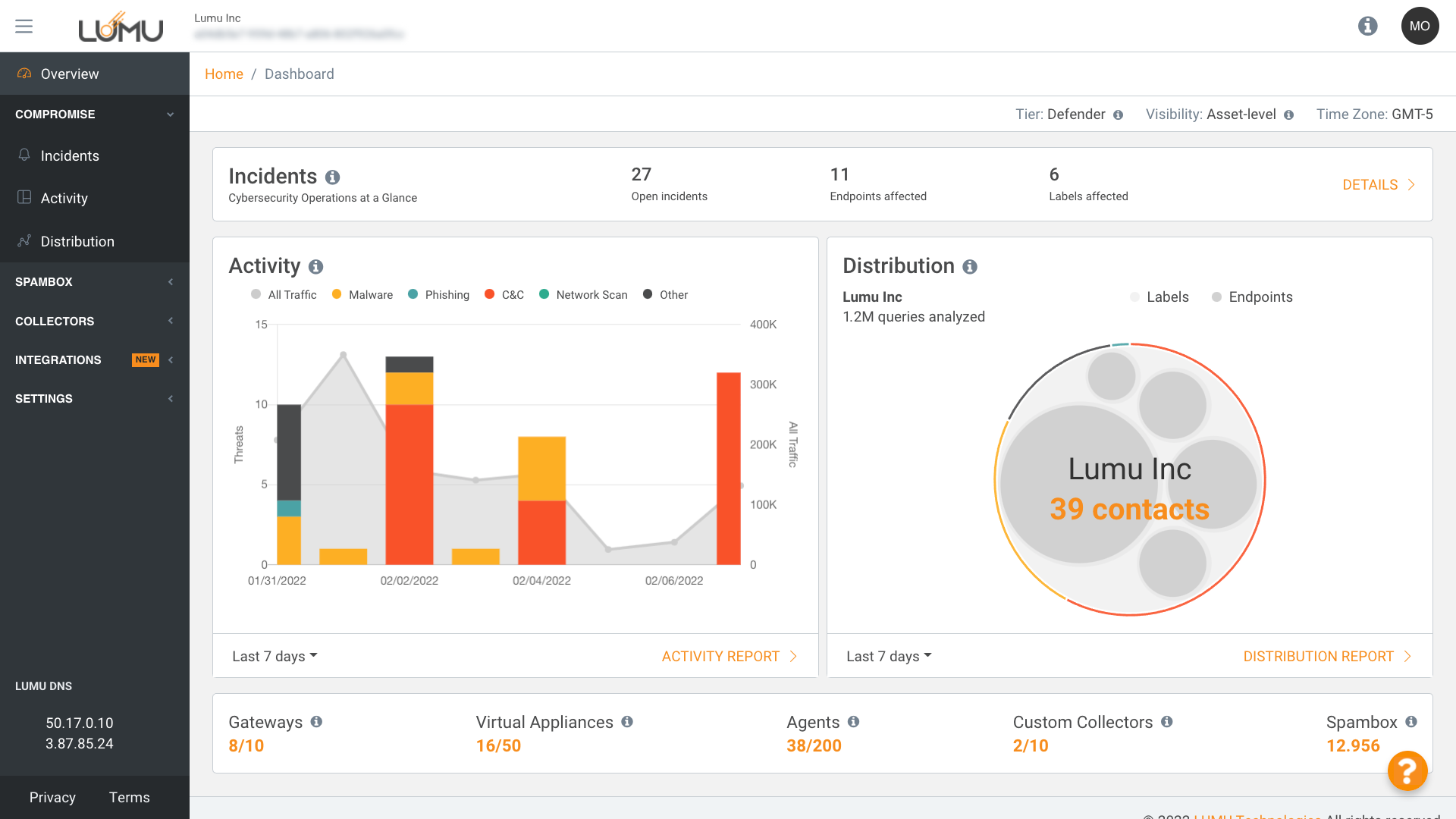
Take a look at how Lumu works.
Want to go even deeper?
Sign up for a live product demo.
Gain an insight into which attack types are more prevalent across your organization so that you may take appropriate action.
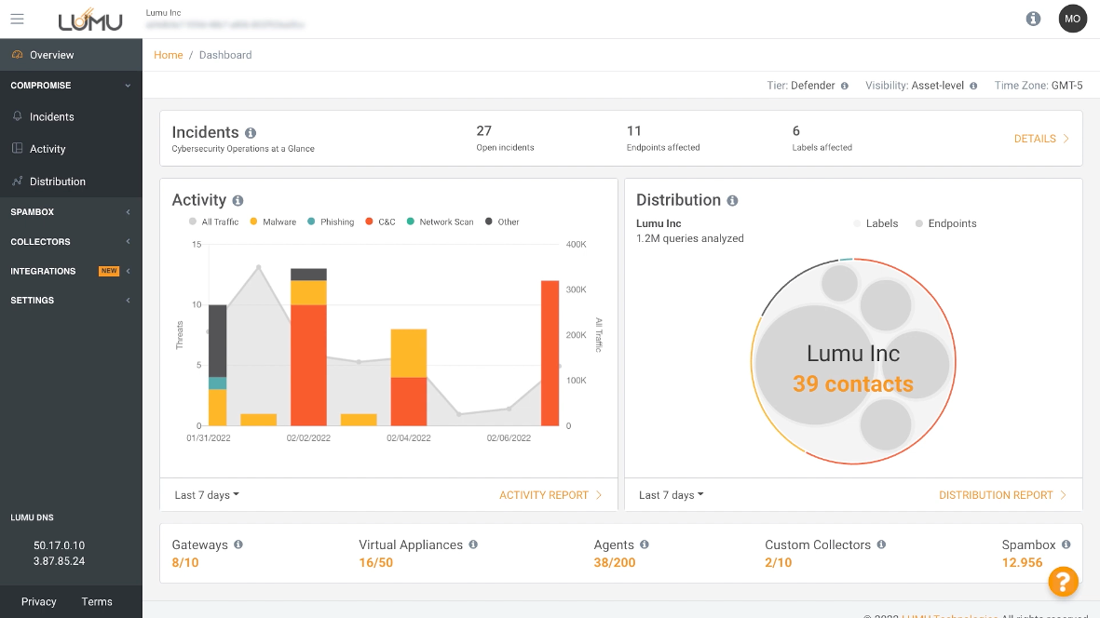
Incidents are created anytime your network is in contact with malicious infrastructure, reporting right when it happens.
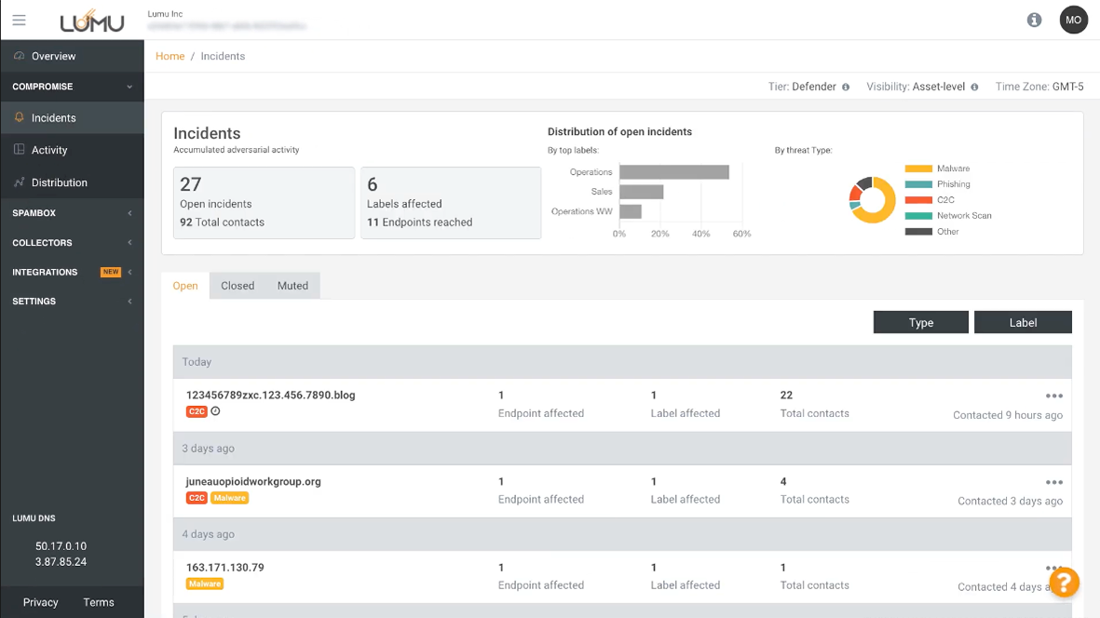
The compromise radar gives in-depth detail about which assets were in contact with malicious IoCs.
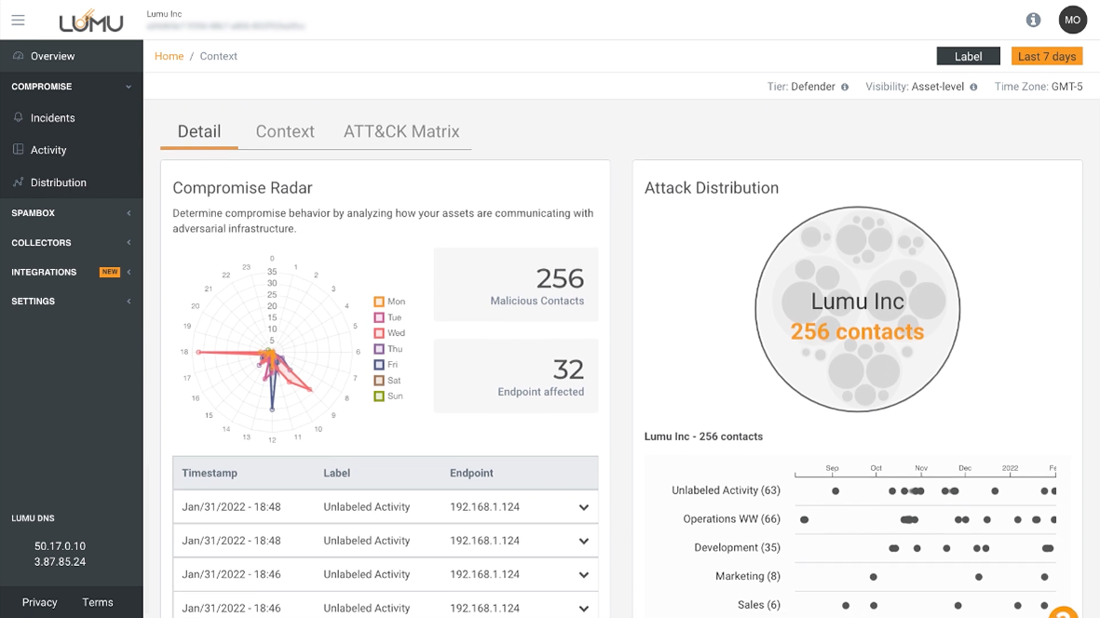
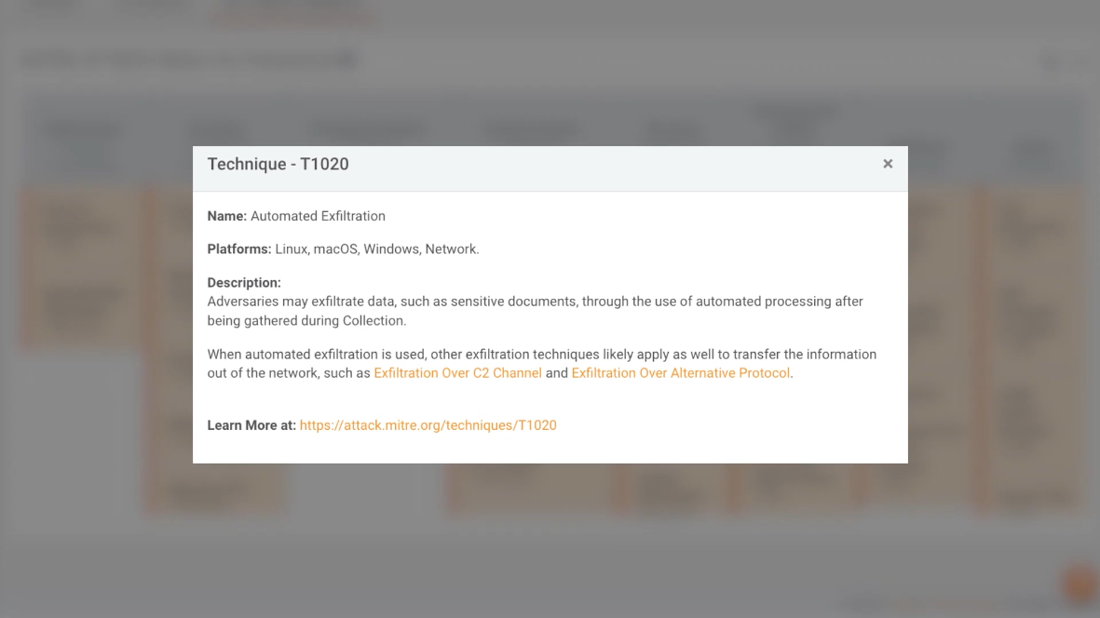
All incidents are linked to the MITRE ATT&CK Matrix to perform faster and more precise threat hunting by understanding how each threat operates and what its end goal is.
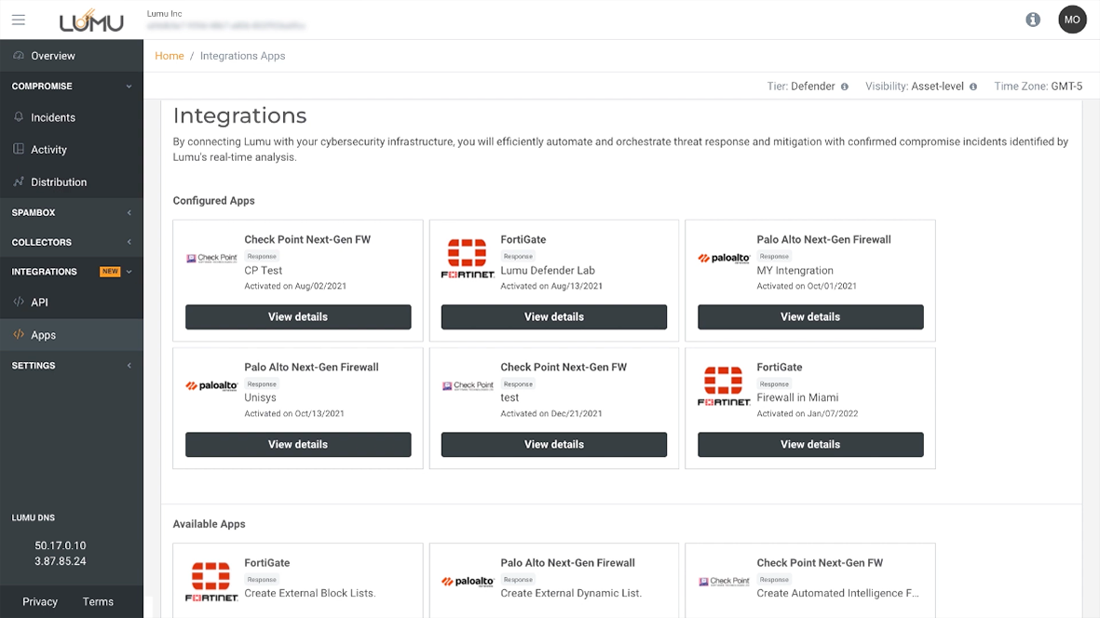
Various out-of-the-box integrations can be seamlessly added to other elements of your cybersecurity stack for real-time action
© Lumu Technologies All rights reserved. | Legal information.