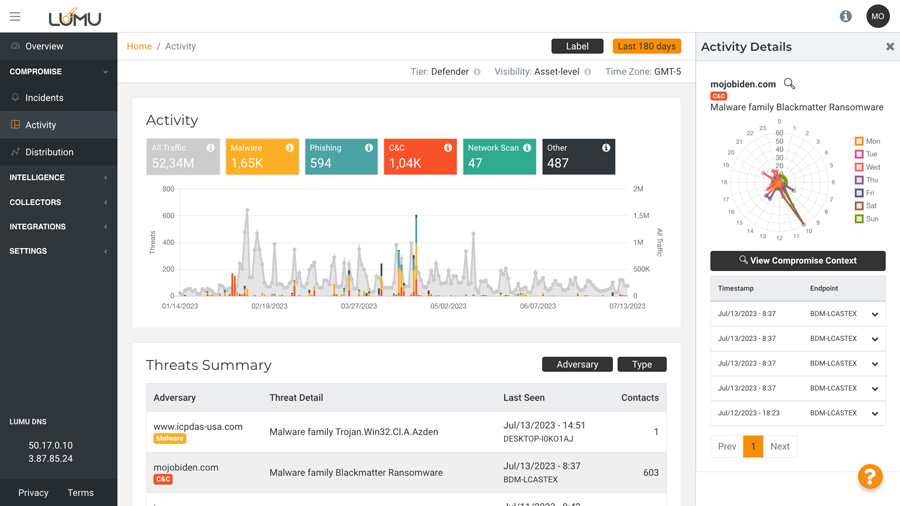
Streamline incident management, improve the analyst experience.

Increase efficiency and save time by prioritizing your most critical incidents.

Get your cybersecurity stack on the same page with our 80+ integrations.

Uncover top attack techniques used to target your organization for a precise response.
Optimize your cybersecurity operation with the ability to sort, filter, and take group actions against threats.
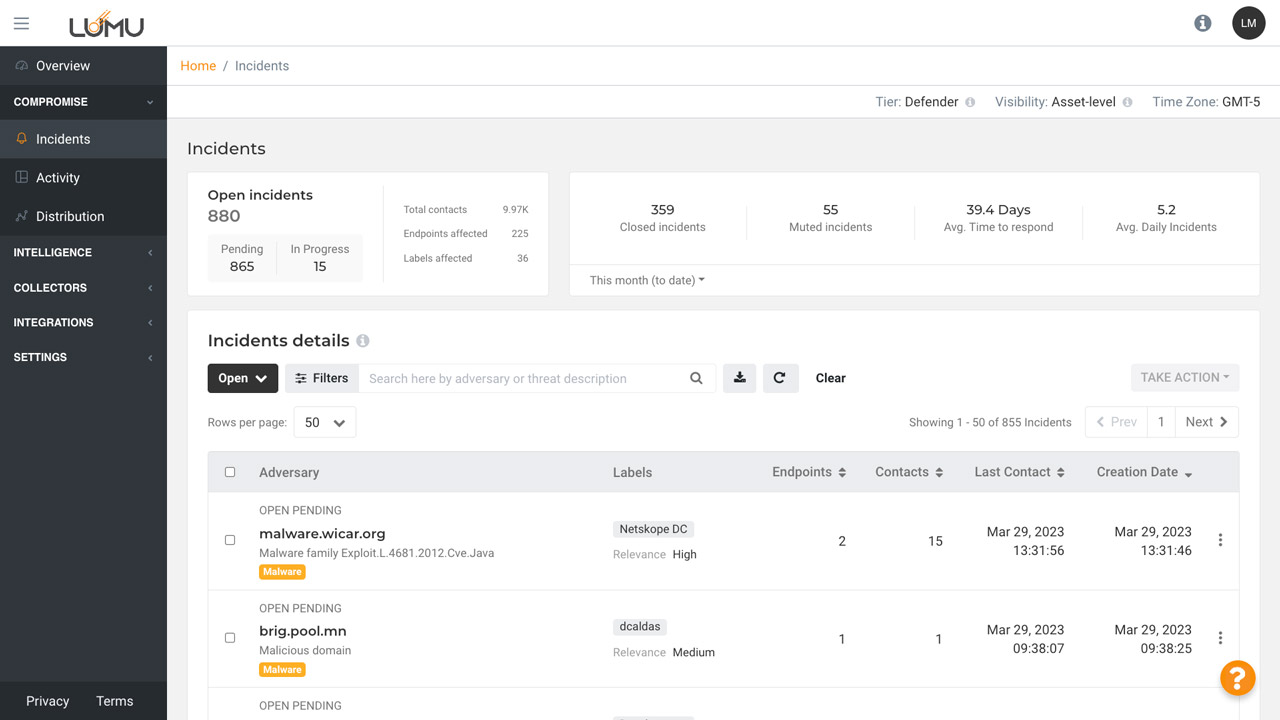
See which incidents are currently open, pending, or in progress.
Number of incidents closed within the selected timeframe below.
Average # of incidents created on a daily basis.
Allows you to select preferred time.
Visualize incidents by their status -open, muted, closed, or all.
Filter incidents based on threat type, labels, contacts and more.
Search for incidents using keywords.
Download incident information based on filters applied.
Take group actions on incidents like closing, muting, or mark pending.
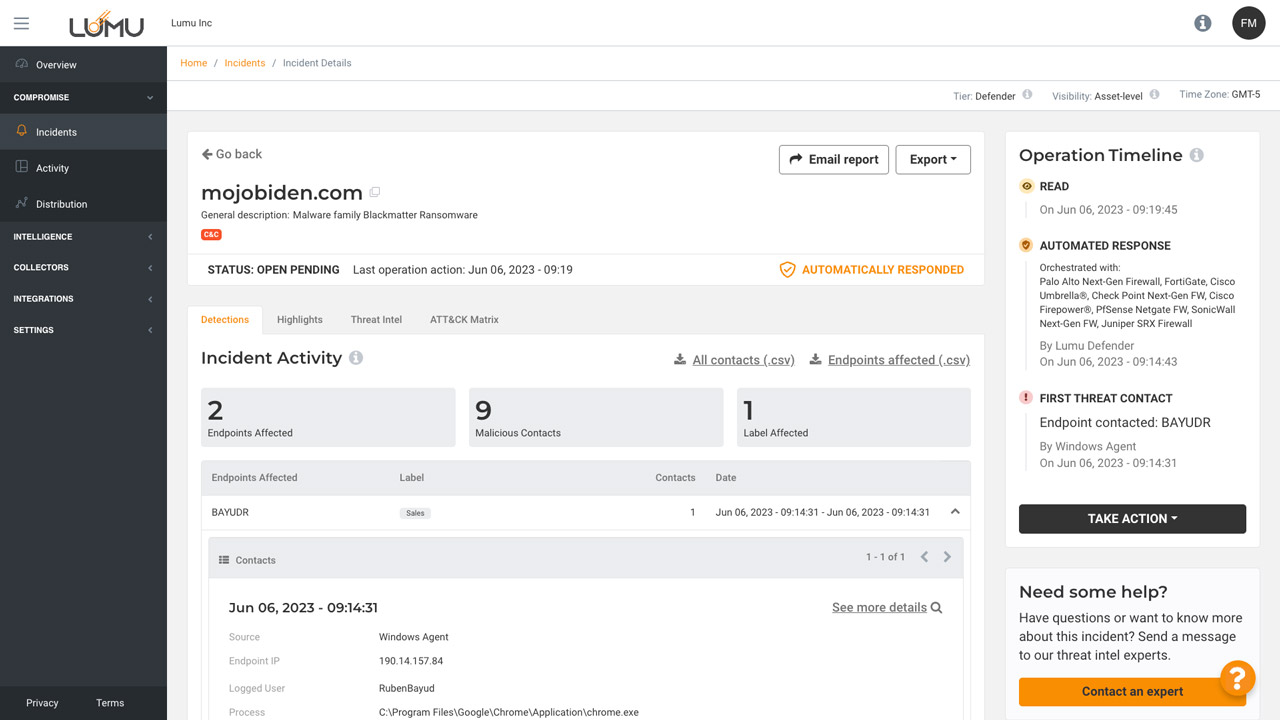
See the name of the IoC and a description of the threat.
Send all of the details and context from an incident to anyone.
Get the context around how your organization is being impacted by adversaries.
Shows how you and your team have responded to the incident.
Take actions within the incident and collaborate as a team.
Extra information from the metadata collector about the threat and the impacted asset.
Each incident provides granular details around malicious activity with the tools to collaborate as a team.
Seamlessly implement Lumu with options for different technical environments.
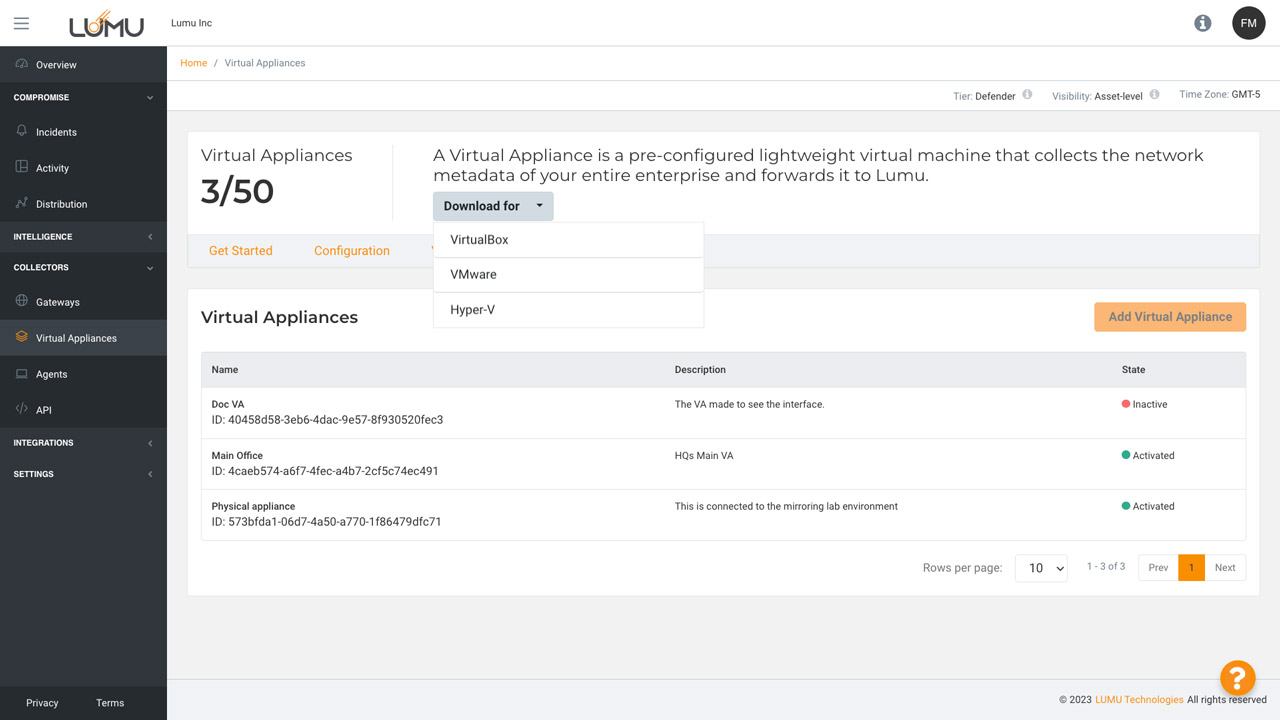
Self-service option for data collection.
Add unlimited virtual appliances for your environment.
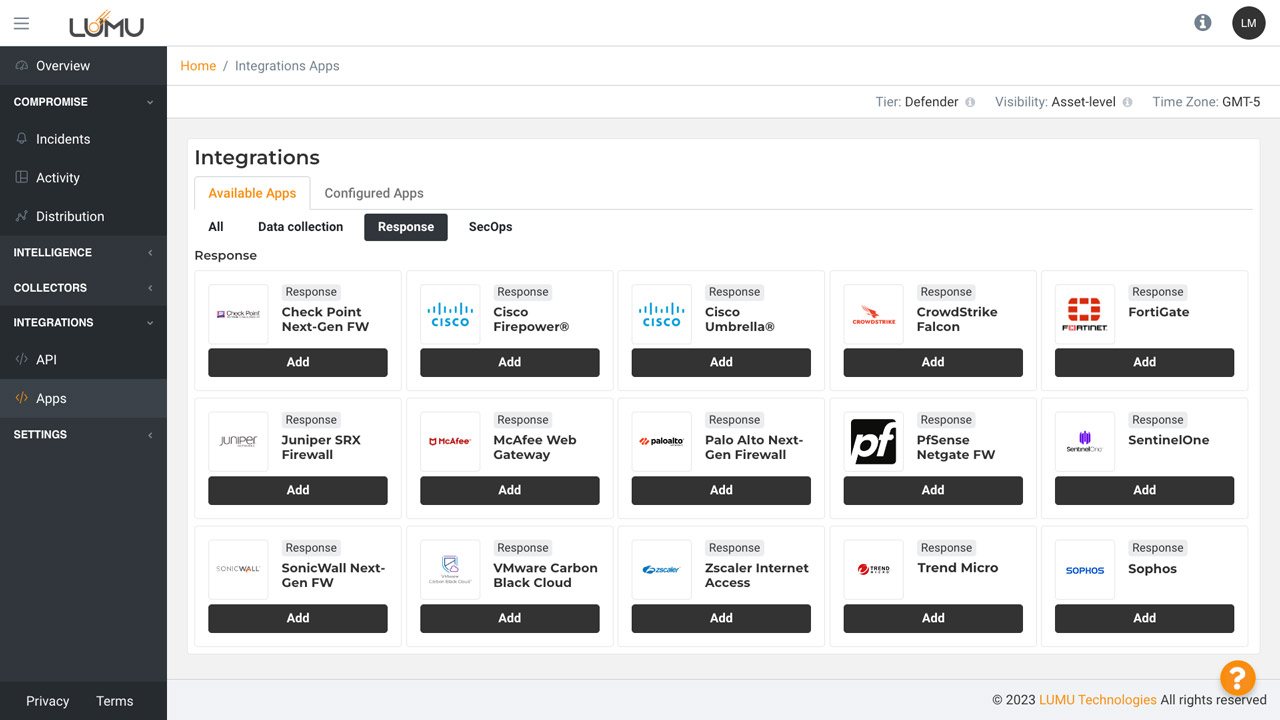
Configure integrations with Lumu’s API
Designate actions against threats with just a few clicks using out-of-the-box integrations.
Select the out-of-the-box integration type.
Click on add to begin configuring your integration with just a few clicks.
Automate incident response with just a few clicks using your existing tools.
Understand how attackers are targeting your organization and the top techniques they are using.
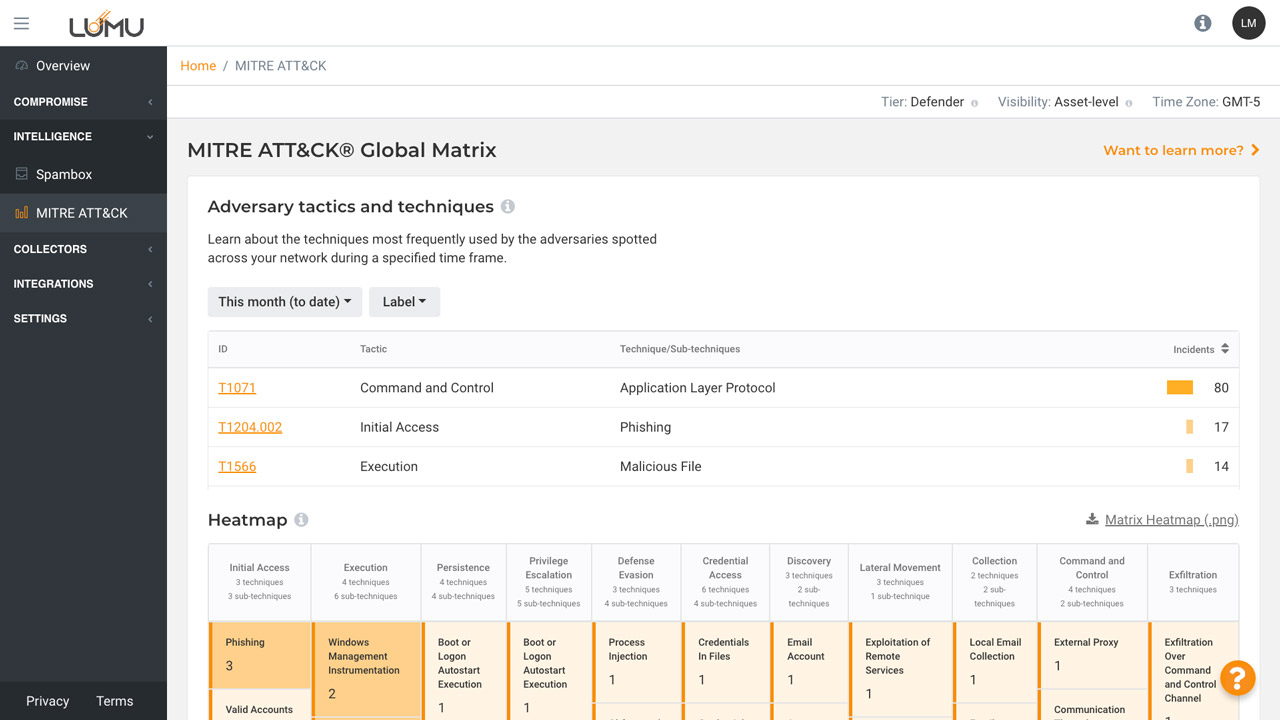
See how attack techniques are most frequently used against your organization.
Filter by labels to prioritize threat types impacting different areas of the business.
Select a timeframe to see the techniques used within a certain period.
See the distribution of techniques within the selected timeframe and prioritize efforts.
Download the heatmap to visualize top attack types and share with others.

BANKING

SVP, Senior Technology Officer
“Lumu catches the things that make it past our other defences. It’s kind of scary – if we didn’t have Lumu, what would we not be seeing?”
Watch Interview
FINANCIAL

Head of Cybersecurity
“Lumu identifies what is failing, against whom you are failing, and how to respond to that failure. Nothing else in the market does this.”
Watch Interview
FINANCIAL

CISO
“Lumu can even see things before my endpoint protection. This is spectacular because I don’t need to activate an endpoint response plan, because I’ve dealt with it before it’s happened.”
Watch Interview
FINANCIAL

Cybersecurity Manager
“Lumu gives you all the information you need to precisely act in a timely manner”
Watch Interview
EDUCATION

Information Systems Director
“Think of a security stack as a stack of Swiss cheese pieces: each piece provides defense, but each one of those layers has holes in it. If a threat gets through, Lumu catches that.”
Watch Interview
EDUCATION

Technology and Facilities Director
“It paired really nicely with our Checkpoint firewall and our CrowdStrike. That interoperability oftentimes doesn’t happen. And so Lumu really makes these other tools that we were using better.”
Watch Interview
EDUCATION

Director of information Services
“Even though we had our security stack in place, those solutions had some gaps. [When we installed Lumu we were seeing some command and control and malware on the servers.”
Watch Interview
STATE & LOCAL GOVERNMENT

Chief Information Officer
“Lumu is making actionable decisions in real-time based on information it’s ingesting from our network, it integrates with our firewall and response happens within seconds.”
Watch Interview
STATE & LOCAL GOVERNMENT

Information Security Officer
“Lumu’s automated response is next generational, we’re not up all night watching monitors to see what’s going on.”
Watch Interview
HEALTHCARE

IT Coordinator
“I had a variable blinspot in my network, one any IT professional would lose sleep over. Lumu comes in, I get it setup, nd I’m able to sleep at night.“
Watch Interview
MSP

Cloud / Security Specialist
“Lumu has been fantastic in it’s flexibility around deployment for different customers.”
Watch Interview
MSP

CEO
“When Lumu sees compromise it will integrate with your other products to automatically block those threats.”
Watch Interview
MSP

Systems Engineer
“Lumu helped us narrow down response efforts to a malicious incident with a client by showing us what happened, seeing which user it involved, the specific IP and device so we could quickly reach out to our client and let them know what was going on.“
Watch Interview
MSP

IT Consultant
“Lumu helps us understand which tools we need in our cyber-stack and whether or not they are actually working.”
Watch Interview
GOVERNMENT

Network Security Analyst
“We previously used a SIEM that complicated things, Lumu gives us clear information we can decisively act on.“
Watch Interview
HEALTHCARE

Director, Information Technology
“Lumu helps us protector our OCB network but also ensures we are securing our HIPAA data being a large healthcare organization.”
Watch Interview
HOSPITALITY

IT Director
“Lumu is easy to install. Since we don’t have a full time cybersecurity person on staff, Lumu has become our virtual cybersecurity analyst.”
Watch Interview
BANKING

SVP, Senior Technology Officer
“Lumu catches the things that make it past our other defences. It’s kind of scary – if we didn’t have Lumu, what would we not be seeing?”
Watch Interview
FINANCIAL

Head of Cybersecurity
“Lumu identifies what is failing, against whom you are failing, and how to respond to that failure. Nothing else in the market does this.”
Watch Interview
FINANCIAL

CISO
“Lumu can even see things before my endpoint protection. This is spectacular because I don’t need to activate an endpoint response plan, because I’ve dealt with it before it’s happened.”
Watch Interview
FINANCIAL

Cybersecurity Manager
“Lumu gives you all the information you need to precisely act in a timely manner”
Watch Interview
EDUCATION

Information Systems Director
“Think of a security stack as a stack of Swiss cheese pieces: each piece provides defense, but each one of those layers has holes in it. If a threat gets through, Lumu catches that.”
Watch Interview
EDUCATION

Technology and Facilities Director
“It paired really nicely with our Checkpoint firewall and our CrowdStrike. That interoperability oftentimes doesn’t happen. And so Lumu really makes these other tools that we were using better.”
Watch Interview
EDUCATION

Director of information Services
“Even though we had our security stack in place, those solutions had some gaps. [When we installed Lumu we were seeing some command and control and malware on the servers.”
Watch Interview
STATE & LOCAL GOVERNMENT

Chief Information Officer
“Lumu is making actionable decisions in real-time based on information it’s ingesting from our network, it integrates with our firewall and response happens within seconds.”
Watch Interview
STATE & LOCAL GOVERNMENT

Information Security Officer
“Lumu’s automated response is next generational, we’re not up all night watching monitors to see what’s going on.”
Watch Interview
HEALTHCARE

IT Coordinator
“I had a variable blinspot in my network, one any IT professional would lose sleep over. Lumu comes in, I get it setup, nd I’m able to sleep at night.“
Watch Interview
MSP

Cloud / Security Specialist
“Lumu has been fantastic in it’s flexibility around deployment for different customers.”
Watch Interview
MSP

CEO
“When Lumu sees compromise it will integrate with your other products to automatically block those threats.”
Watch Interview
MSP

Systems Engineer
“Lumu helped us narrow down response efforts to a malicious incident with a client by showing us what happened, seeing which user it involved, the specific IP and device so we could quickly reach out to our client and let them know what was going on.“
Watch Interview
MSP

IT Consultant
“Lumu helps us understand which tools we need in our cyber-stack and whether or not they are actually working.”
Watch Interview
GOVERNMENT

Network Security Analyst
“We previously used a SIEM that complicated things, Lumu gives us clear information we can decisively act on.“
Watch Interview
HEALTHCARE

Director, Information Technology
“Lumu helps us protector our OCB network but also ensures we are securing our HIPAA data being a large healthcare organization.”
Watch Interview
HOSPITALITY

IT Director
“Lumu is easy to install. Since we don’t have a full time cybersecurity person on staff, Lumu has become our virtual cybersecurity analyst.”
Watch Interview
BANKING

SVP, Senior Technology Officer
“Lumu catches the things that make it past our other defences. It’s kind of scary – if we didn’t have Lumu, what would we not be seeing?”
Watch InterviewTake a look at how Lumu works.
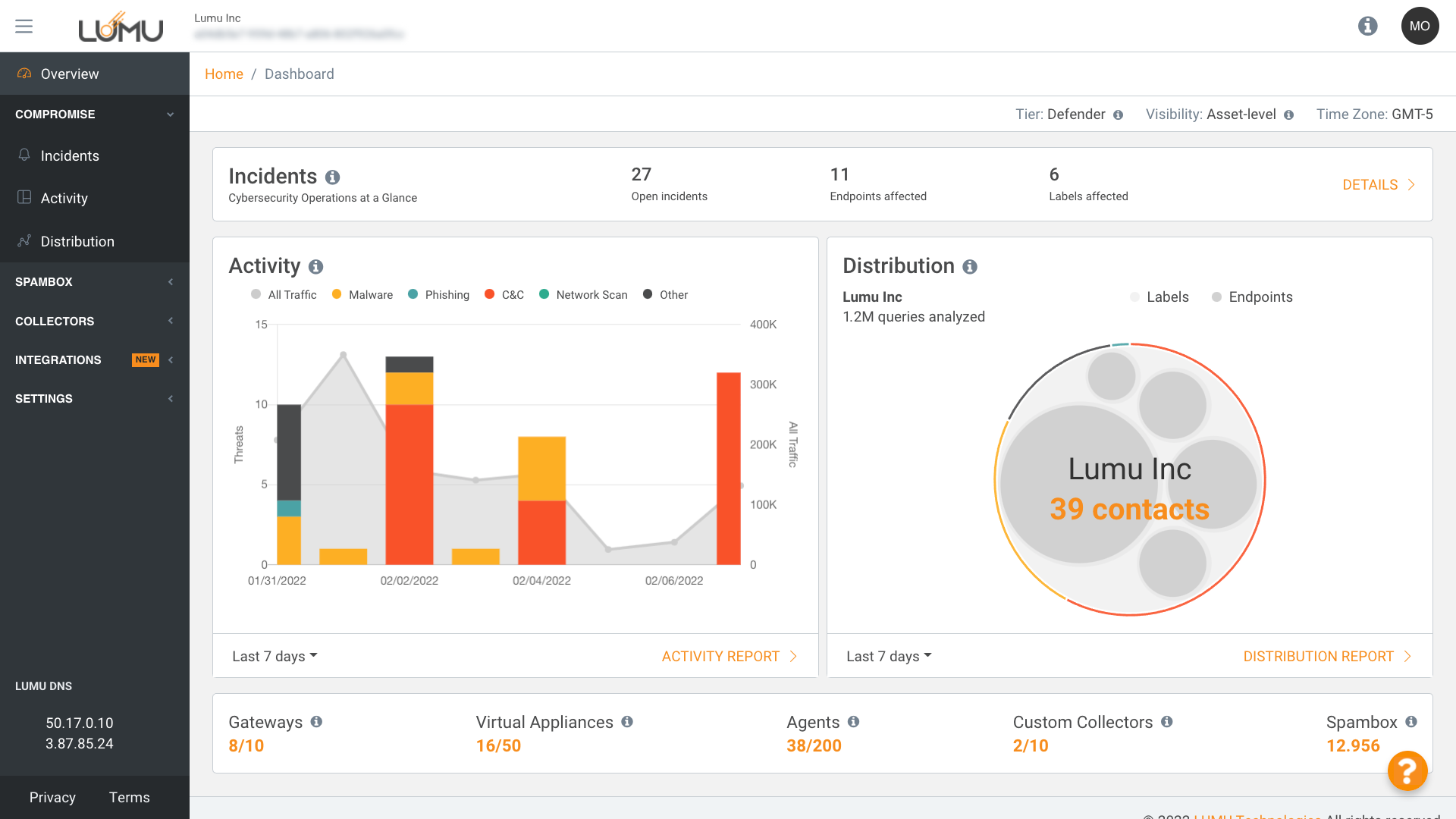
Want to go even deeper?
Sign up for a live product demo.
© Lumu Technologies All rights reserved. | Legal information.