K–12 Schools face unique threats and challenges. Lumu helps you protect student data and network infrastructure.
While these tools are essential components of a cybersecurity stack, they have their shortcomings and are known to be easy targets for cyber criminals.
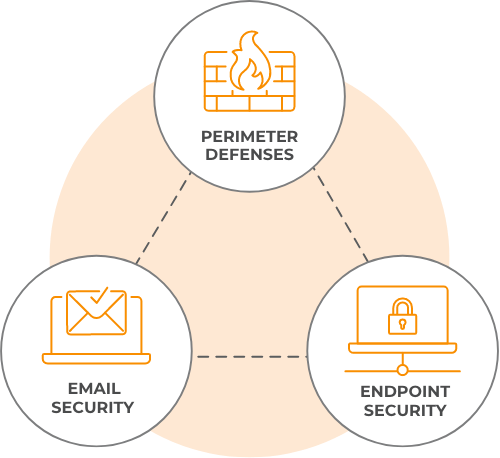
Cybercriminals target schools because student data is valuable. They know that traditional defenses can be bypassed and that small teams oversee networks the size of big enterprises.
Lumu gives K–12 full network visibility and empowers them to detect and respond to threats in real time. Aligned with the NIST cybersecurity framework, Lumu helps optimize security operations.


Nasville, TE

Information Systems Director
“Think of a security stack as a stack of Swiss cheese pieces: each piece provides defense, but each one of those layers has holes in it. If a threat gets through, Lumu catches that.”
Watch Interview
Evanston, WY

Technology and Facilities Director
“It paired really nicely with our Checkpoint firewall and our CrowdStrike. That interoperability oftentimes doesn’t happen. And so Lumu really makes these other tools that we were using better.”
Watch Interview
Pinedale, WY

Director of information Services
“Even though we had our security stack in place, those solutions had some gaps. [When we installed Lumu we were seeing some command and control and malware on the servers.”
Watch Interview
Nasville, TE

Information Systems Director
“Think of a security stack as a stack of Swiss cheese pieces: each piece provides defense, but each one of those layers has holes in it. If a threat gets through, Lumu catches that.”
Watch Interview
Evanston, WY

Technology and Facilities Director
“It paired really nicely with our Checkpoint firewall and our CrowdStrike. That interoperability oftentimes doesn’t happen. And so Lumu really makes these other tools that we were using better.”
Watch Interview
Pinedale, WY

Director of information Services
“Even though we had our security stack in place, those solutions had some gaps. [When we installed Lumu we were seeing some command and control and malware on the servers.”
Watch InterviewTake a look at how Lumu works.
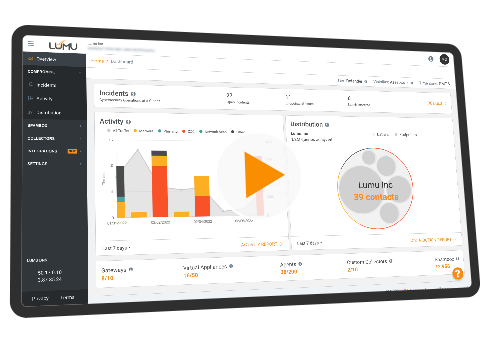
Want to go even deeper?
Sign up for a live product demo.
© Lumu Technologies All rights reserved. | Legal information.