
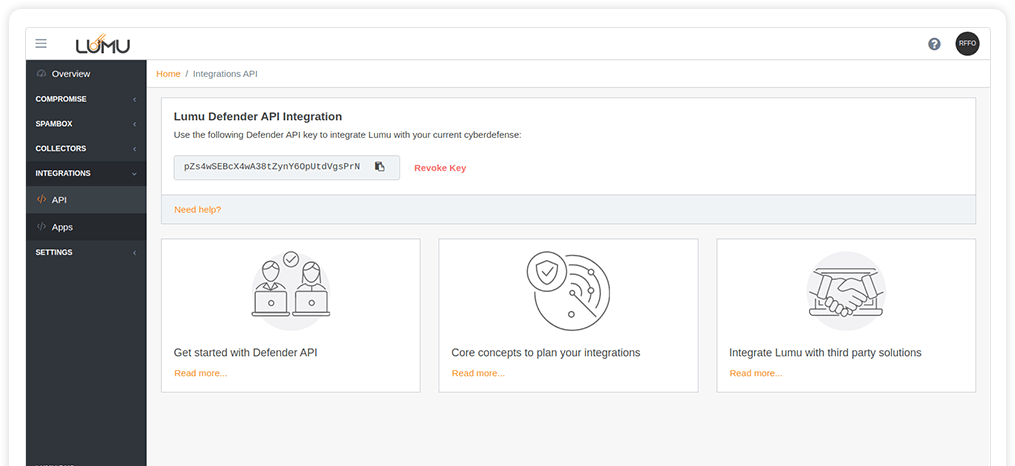
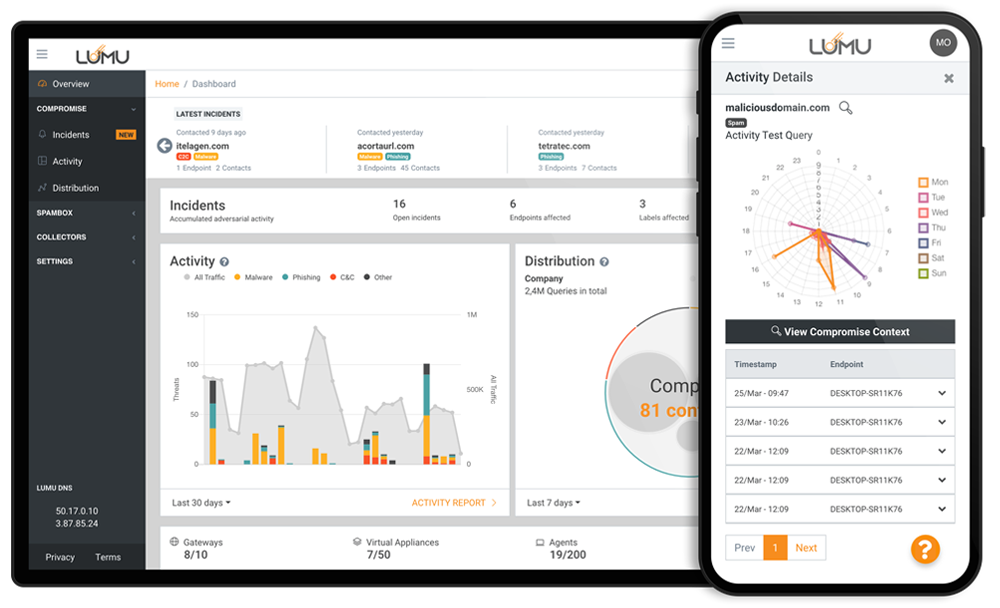
A proficient cybersecurity operation requires collecting information on the cybersecurity architecture’s performance and using that information to continuously improve the system. Lumu lets you automate your response and shorten the threat actor’s window of opportunity.


© Lumu Technologies All rights reserved. | Legal information.