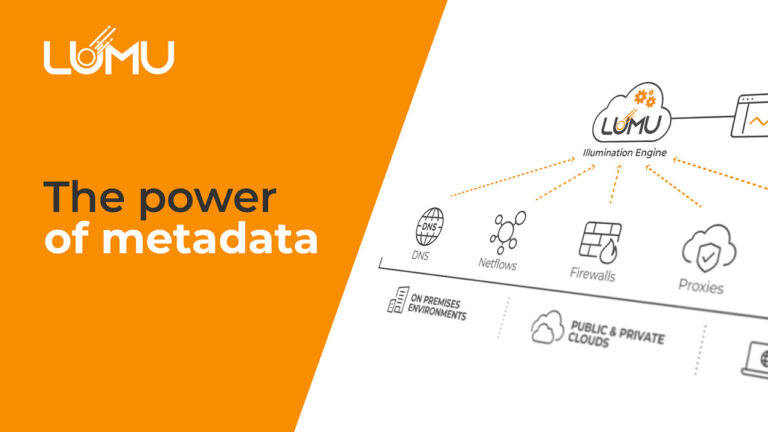
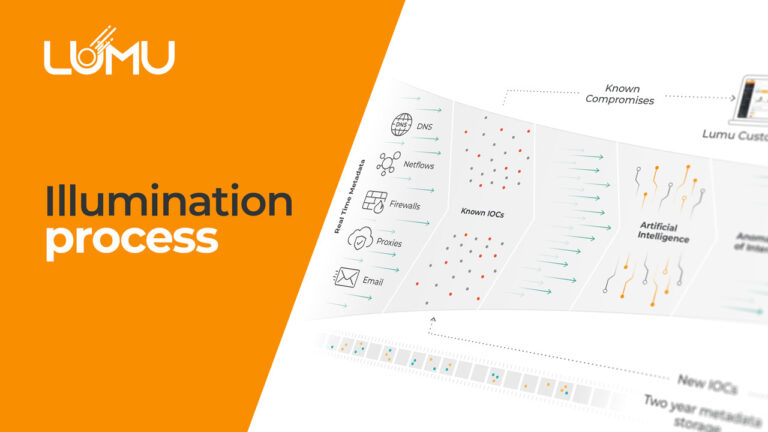
Despite ever-increasing cybersecurity budgets, we continue to see a growing amount of breaches. Cybersecurity architectures are growing in complexity, layering additional tools in the hope that spending more will deliver results. In this video we examine how the cybersecurity architecture can be viewed as a system. That system and its components can be optimized by measuring the outputs of the system. Ultimately, this process leads to the goal of any cybersecurity system: a state of zero compromises.
Already have an account? Sign in
Sign in