
The powerful capabilities our customers value most.

Augment the capabilities of current cybersecurity investments with confirmed compromise information.
Learn more
Custom and out-of-the-box integrations let you connect any tool in your existing cybersecurity stack.
Learn more

Supercharge threat hunting with the MITRE ATT&CK Matrix—now automated directly in the Lumu Portal
Learn more

Remote workers present a great risk to the organization. Quickly and easily discover their device compromise levels and obtain the intelligence to act on it.
Learn more

Arm your security team with factual compromise data that enables them to implement a precise response in a timely manner.
Learn more

Blocking spam is good, but analyzing it is better, because you can discover who is targeting your organization, how they are doing it, and how successful they are.
Learn more
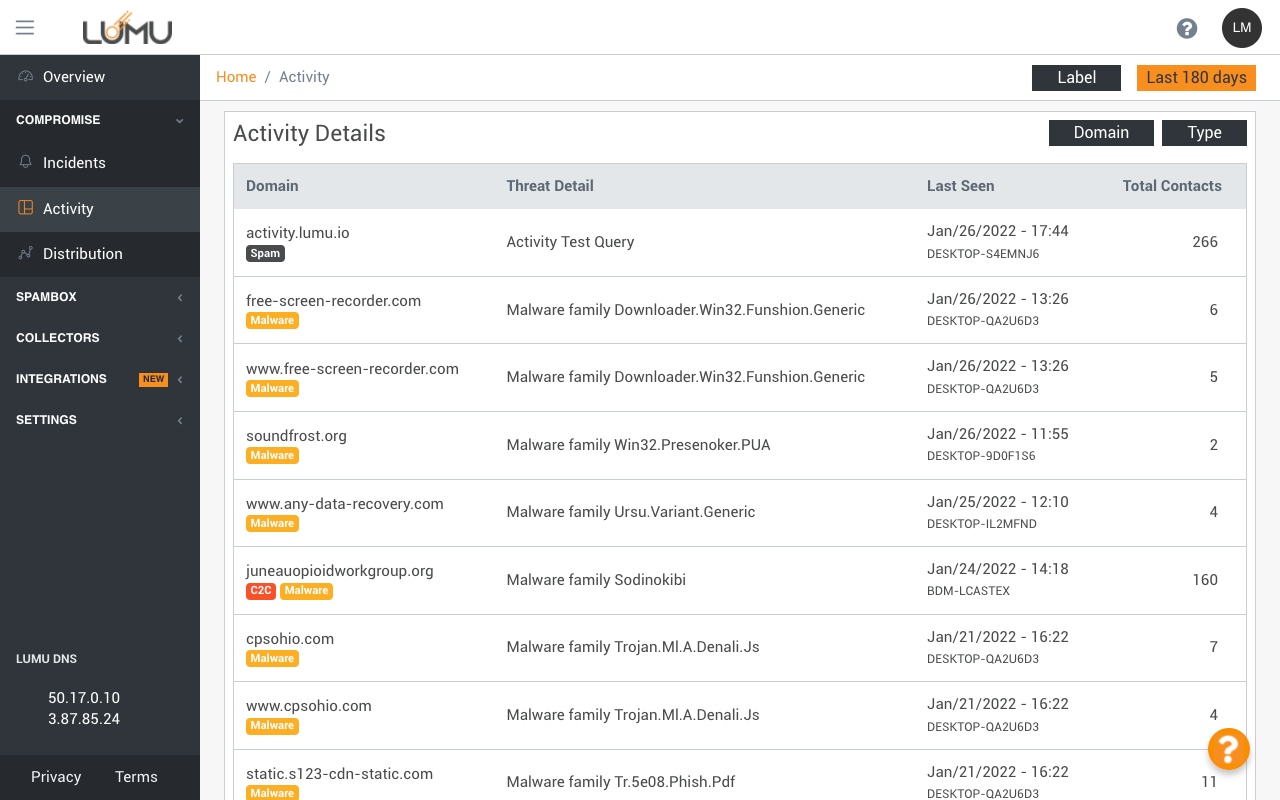
Detailed information about
your state of compromise
Last detected connection
with malicious infrastructure
Flexible filters
Contact with adversarial
infrastructure
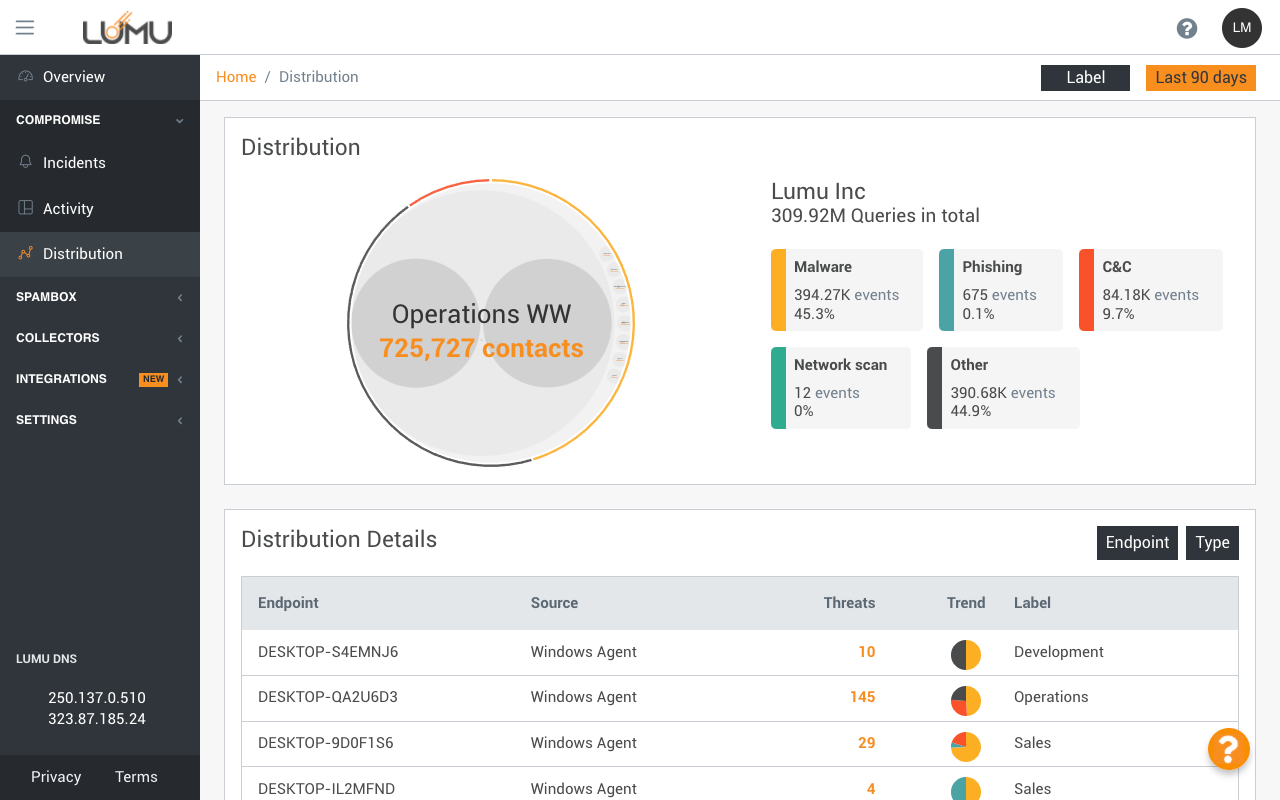
Flexible labeling visualization
that helps prioritize incidents
affecting critical
environments, like PCI,
SWIFT, IOTs, etc.
Environments under
attack, threat details
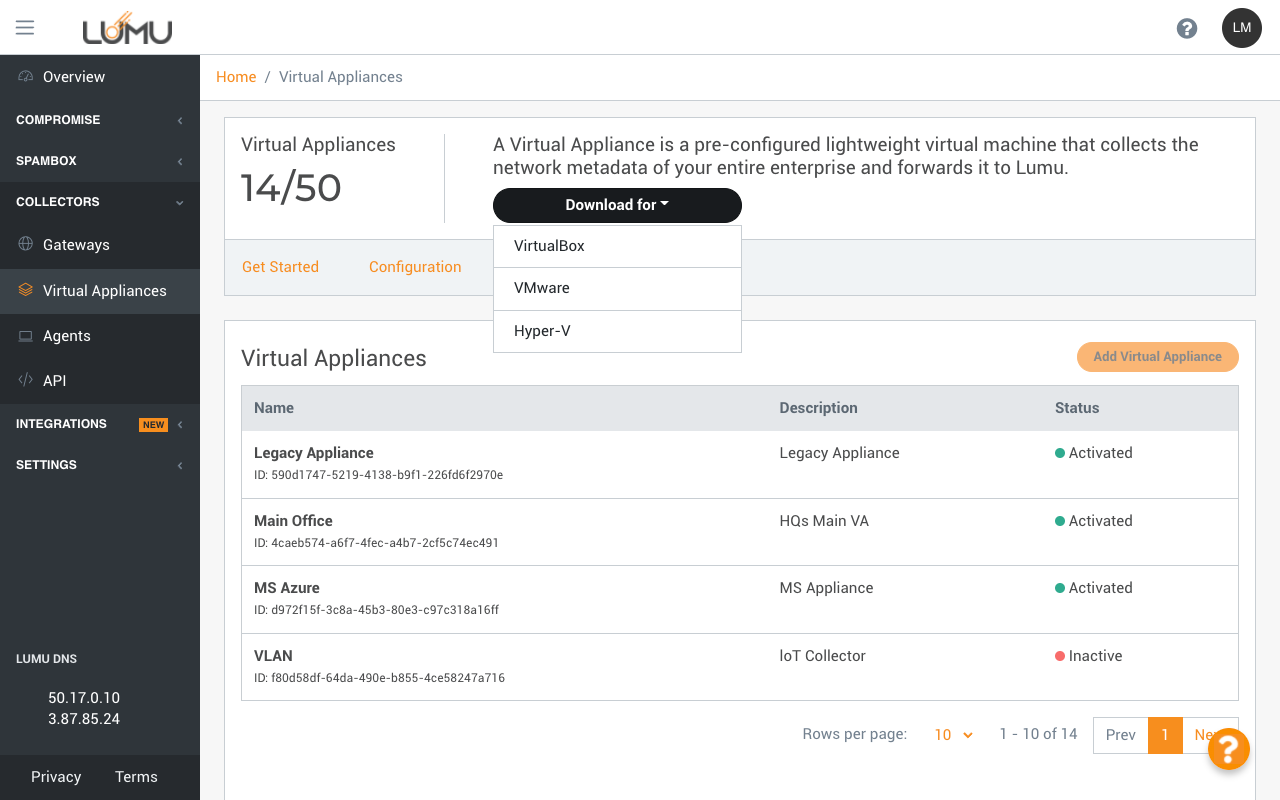
Self-service option for
data collection
Add unlimited Virtual
Appliances for Lumu Insights
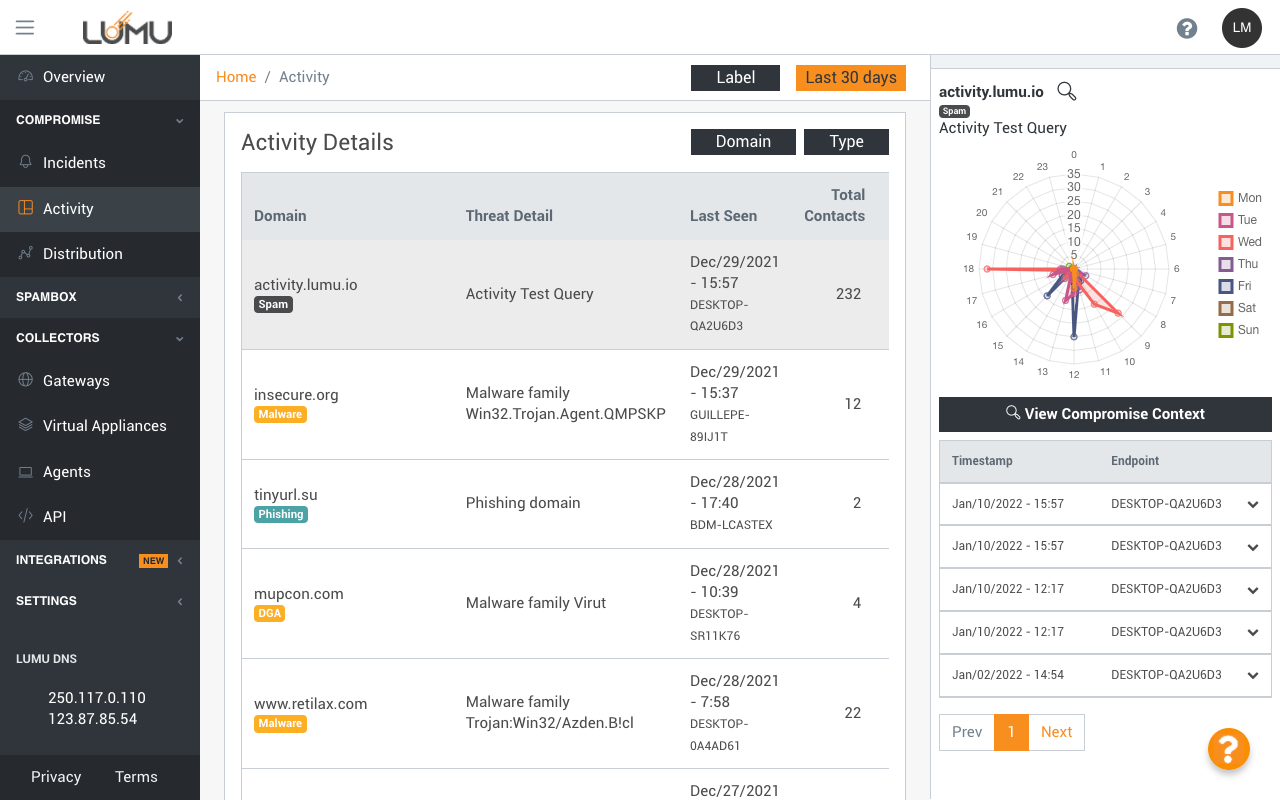
Affected endpoints and
malicious contact generated
for quick, effective decision
making
Conclusive evidence on
compromise behavior
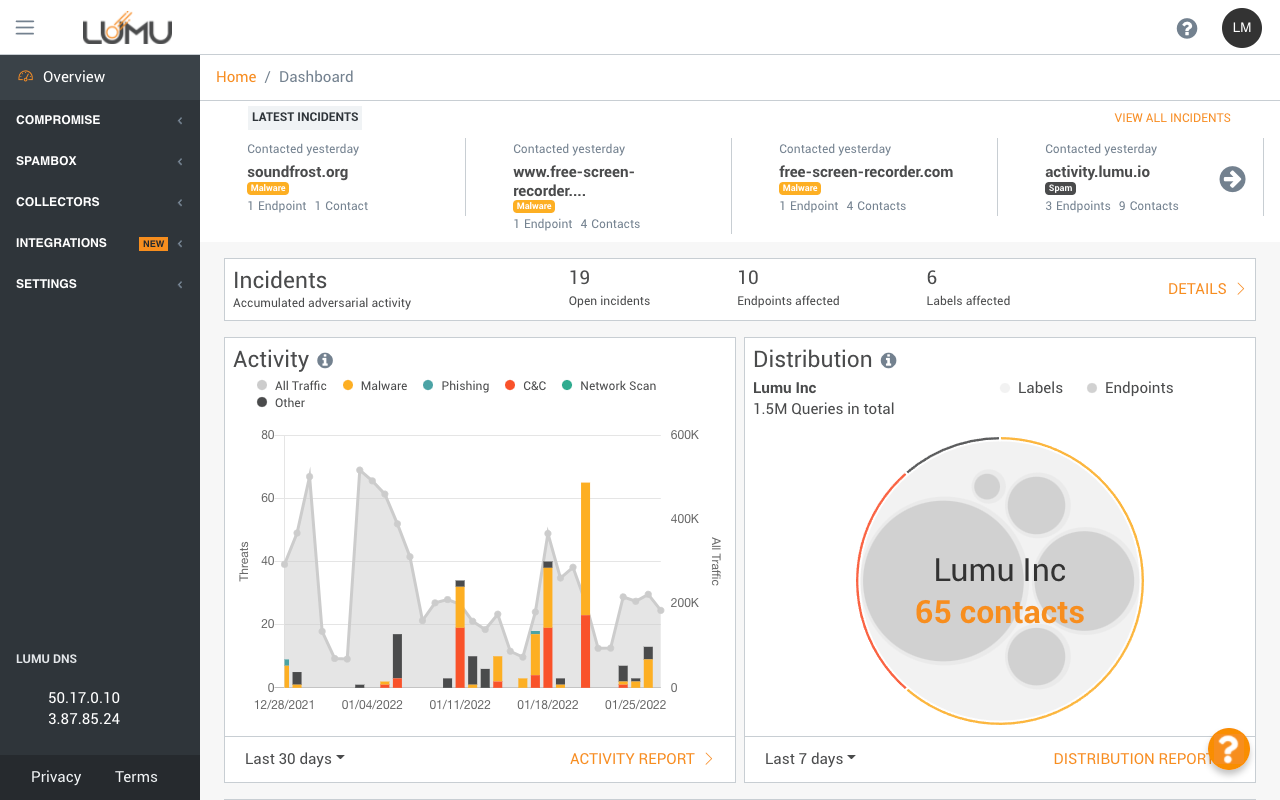
See your compromise
baseline at a glance
Drill down for more
details as needed
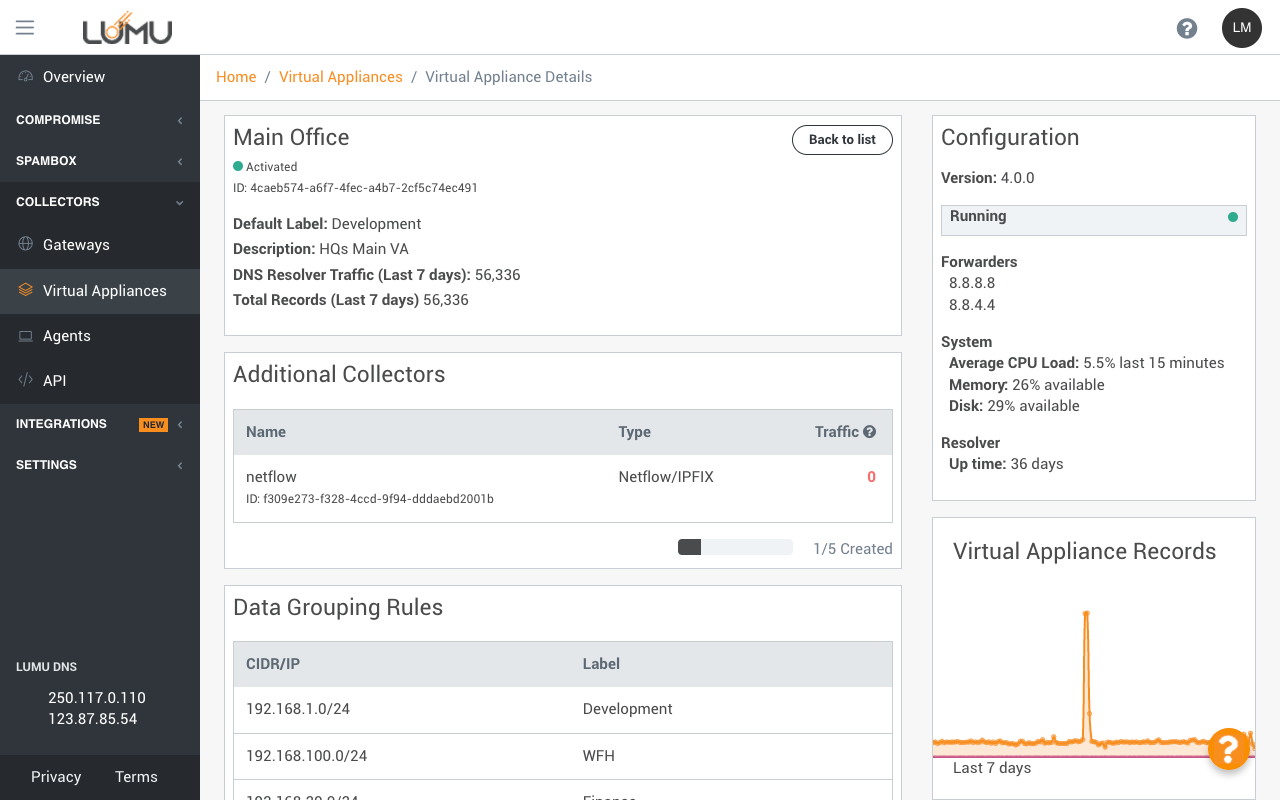
Easily check that your collectors
are functioning properly
Verify collector
key metrics
Deploy collectors for proxy,
firewall and network flow
metadata
Control collectors
configuration

Set up custom
integrations via API
Connect your cybersecurity
stack with a few clicks
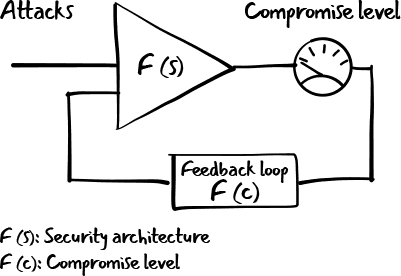
The devil is in the data. Your metadata, that is. Lumu’s Continuous Compromise Assessment model is made possible by its ability to collect, normalize and analyze a wide range of network metadata, including DNS, Netflows, Proxy and Firewall Access Logs and Spambox. The level of visibility that only these data sources provide, allows us to understand the behavior of your enterprise network, which leads to conclusive evidence on your unique compromise levels.
Lumu’s Continuous Compromise Assessment is enabled by our patent-pending Illumination Process. Learn more about how this process uses network metadata and advanced analytics to illuminate your network’s dark spots.
Compromise is infrastructure agnostic. So, collecting network metadata across your complex, hybrid model is essential. Let us walk you through the simple steps to configure Lumu and start measuring compromise immediately.
Continuous Compromise Assessment has received recognition from leading security analysts.
© Lumu Technologies All rights reserved. | Legal information.