
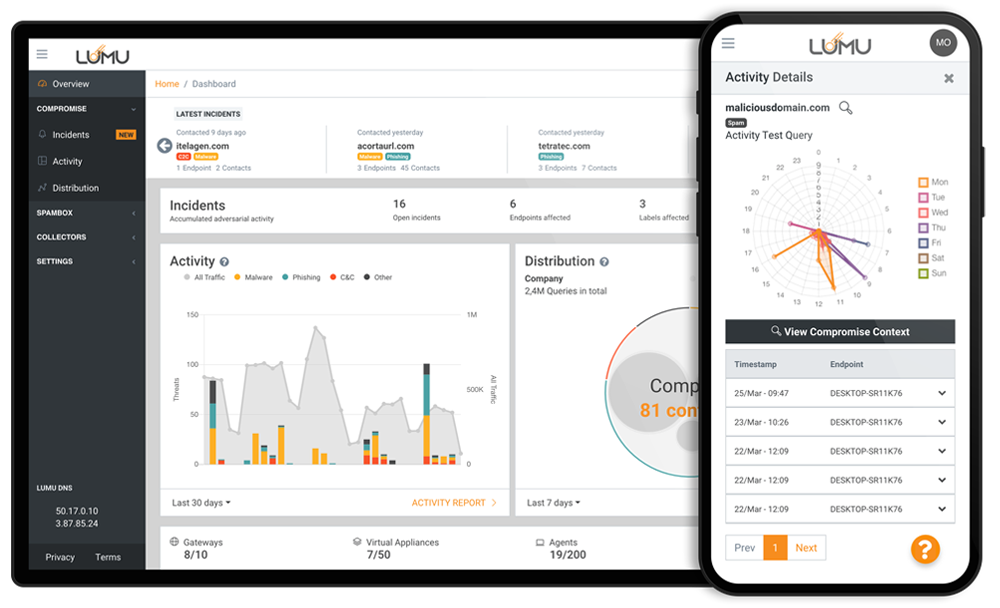
This is your key to improve security daily operations. Compromise Context gives you the intelligence to immediately employ the right response to threats.
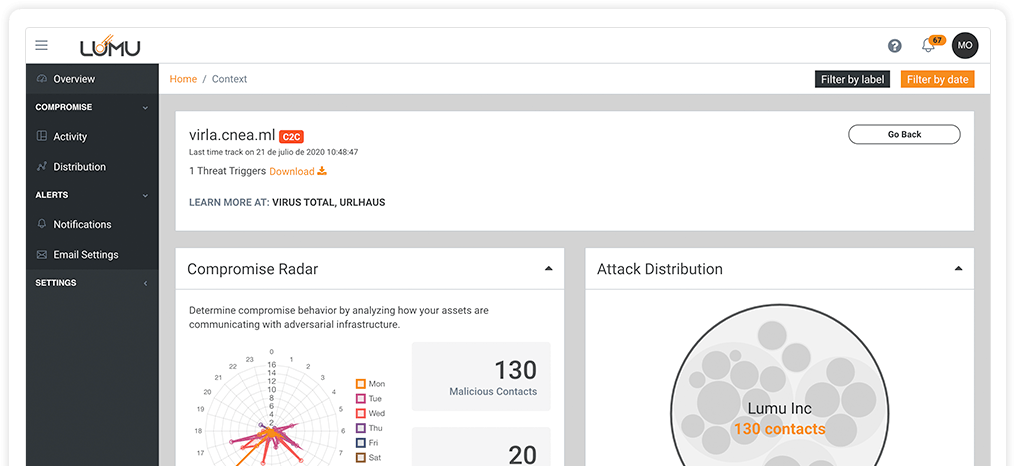
Understand patterns of
confirmed compromises
Differentiate between automatic
and manual contacts
Affected endpoints and malicious
contact generated for quick,
effective decision making
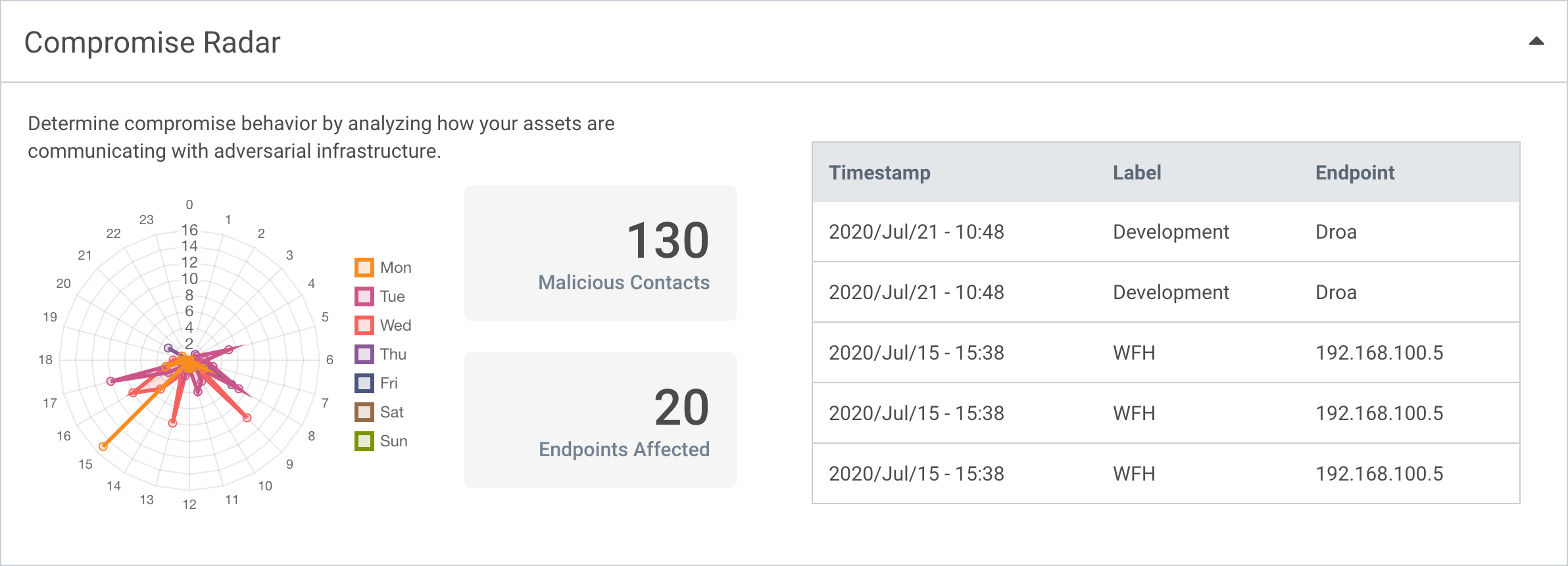
Access flexible
labeling visualization
Identify which assets
are compromised
Discover lateral
movement patterns
within the organization
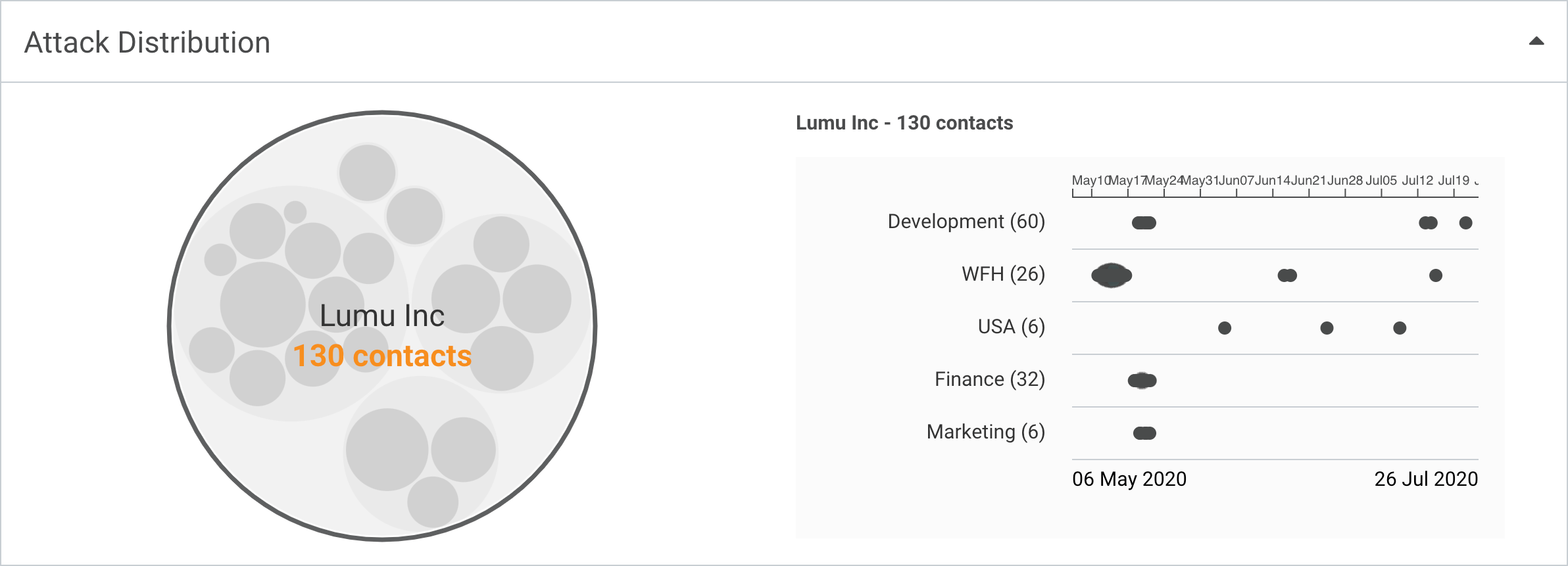
Download IoCs to integrate
with other cybersecurity tools
Gain rich information on
attack history and conditions
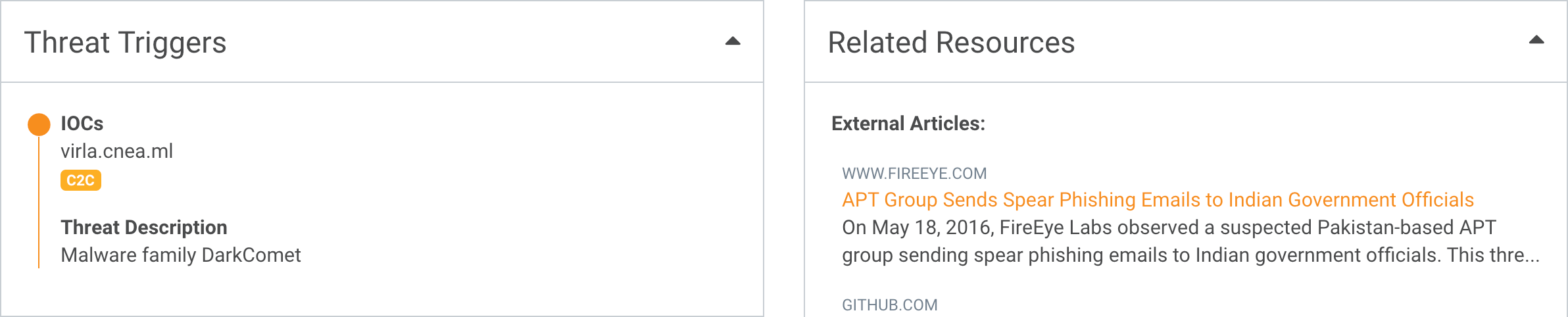
Effective resources to
learn compromise nature
© Lumu Technologies All rights reserved. | Legal information.