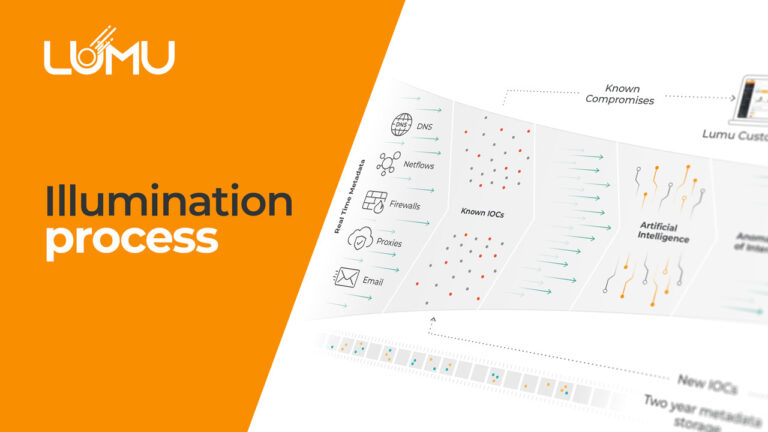
The devil is in the data. Your own network metadata is the single source of truth of your organization’s compromise posture. Lumu’s Continuous Compromise Assessment model is made possible by its ability to collect, normalize and analyze a wide range of network metadata, including DNS, Network Flows, Proxy and Firewall Access Logs and Email. The level of visibility that only these data sources provide, allows us to understand the behavior of your enterprise network, which leads to conclusive evidence on your unique compromise levels.