Cybercriminals constantly develop new ways to bypass EDRs, regardless of the solution.
Watch these videos to see experts bypassing EDRs step-by-step.
Most EDR solutions, while valuable for responding to threats, leave blind spots that attackers often exploit in the network.
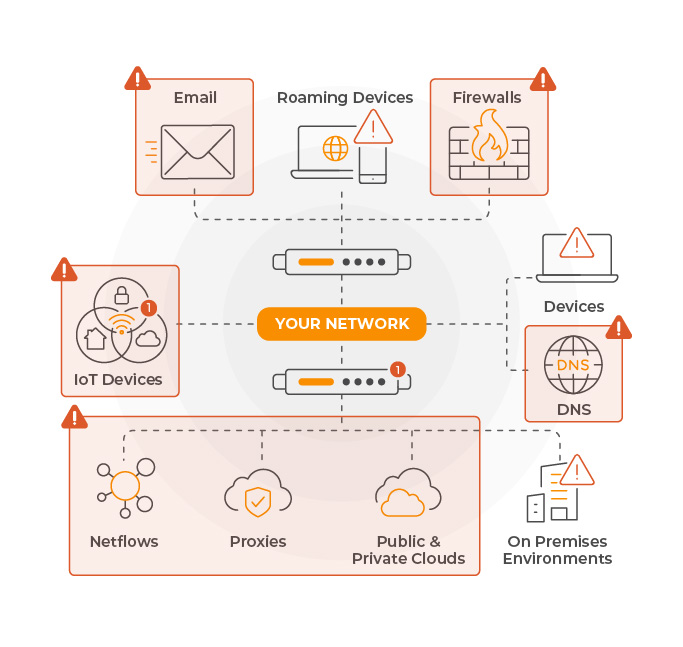
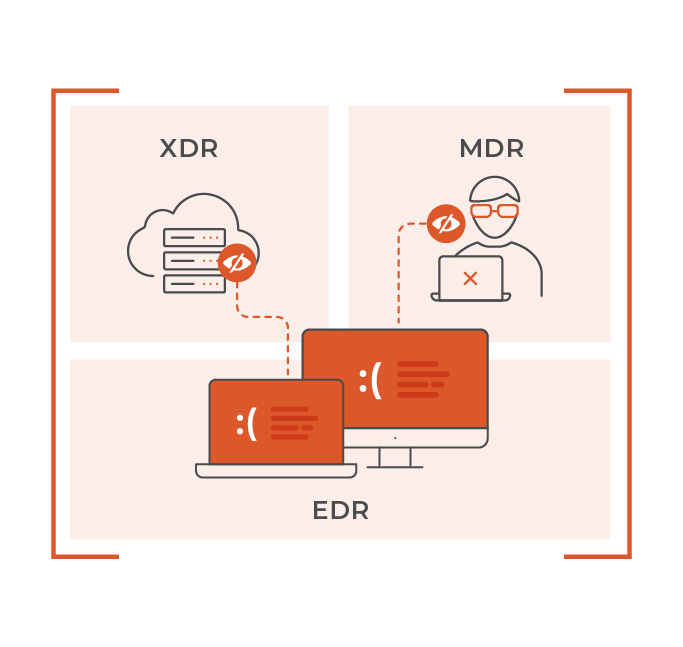
Because XDR and MDR solutions depend on visibility provided by EDRs, they are equally susceptible to evasion.
Lumu continuously analyzes metadata across the entire network to identify threats and orchestrates actions to other elements of your cyber stack for real-time response against attacks.
By continuously analyzing metadata across the entire network to identify threats, Lumu orchestrates responses to the cyber stack for real-time responses against attacks
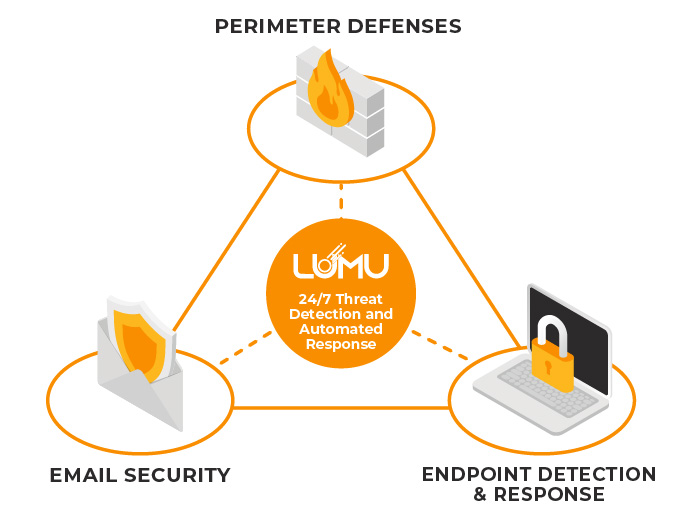
Take a deep dive into the tactics and techniques attackers are using to bypass EDR tools.


Michigan City, IN

SVP, Senior Technology Officer
“Lumu catches the things that make it past our other defences. It’s kind of scary – if we didn’t have Lumu, what would we not be seeing?”
Watch Interview
Brazil

CISO
“Lumu can even see things before my endpoint protection. This is spectacular because I don’t need to activate an endpoint response plan, because I’ve dealt with it before it’s happened.”
Watch Interview
Nasville, TE

Information Systems Director
“Think of a security stack as a stack of Swiss cheese pieces: each piece provides defense, but each one of those layers has holes in it. If a threat gets through, Lumu catches that.”
Watch Interview
Pinedale, WY

Director of information Services
“Even though we had our security stack in place, those solutions had some gaps. [When we installed Lumu we were seeing some command and control and malware on the servers.”
Watch Interview
Michigan City, IN

SVP, Senior Technology Officer
“Lumu catches the things that make it past our other defences. It’s kind of scary – if we didn’t have Lumu, what would we not be seeing?”
Watch Interview
Brazil

CISO
“Lumu can even see things before my endpoint protection. This is spectacular because I don’t need to activate an endpoint response plan, because I’ve dealt with it before it’s happened.”
Watch Interview
Nasville, TE

Information Systems Director
“Think of a security stack as a stack of Swiss cheese pieces: each piece provides defense, but each one of those layers has holes in it. If a threat gets through, Lumu catches that.”
Watch Interview
Pinedale, WY

Director of information Services
“Even though we had our security stack in place, those solutions had some gaps. [When we installed Lumu we were seeing some command and control and malware on the servers.”
Watch Interview
Michigan City, IN

SVP, Senior Technology Officer
“Lumu catches the things that make it past our other defences. It’s kind of scary – if we didn’t have Lumu, what would we not be seeing?”
Watch Interview
Brazil

CISO
“Lumu can even see things before my endpoint protection. This is spectacular because I don’t need to activate an endpoint response plan, because I’ve dealt with it before it’s happened.”
Watch InterviewStories
© Lumu Technologies All rights reserved. | Legal information.
