
Hunt across all your assets and environments.

Keep teams informed about how current defenses are being bypassed.

Leverage hypotheses, IOCs, and AI with retrospective hunting.
Automate defense orchestration with current cybersecurity stack.
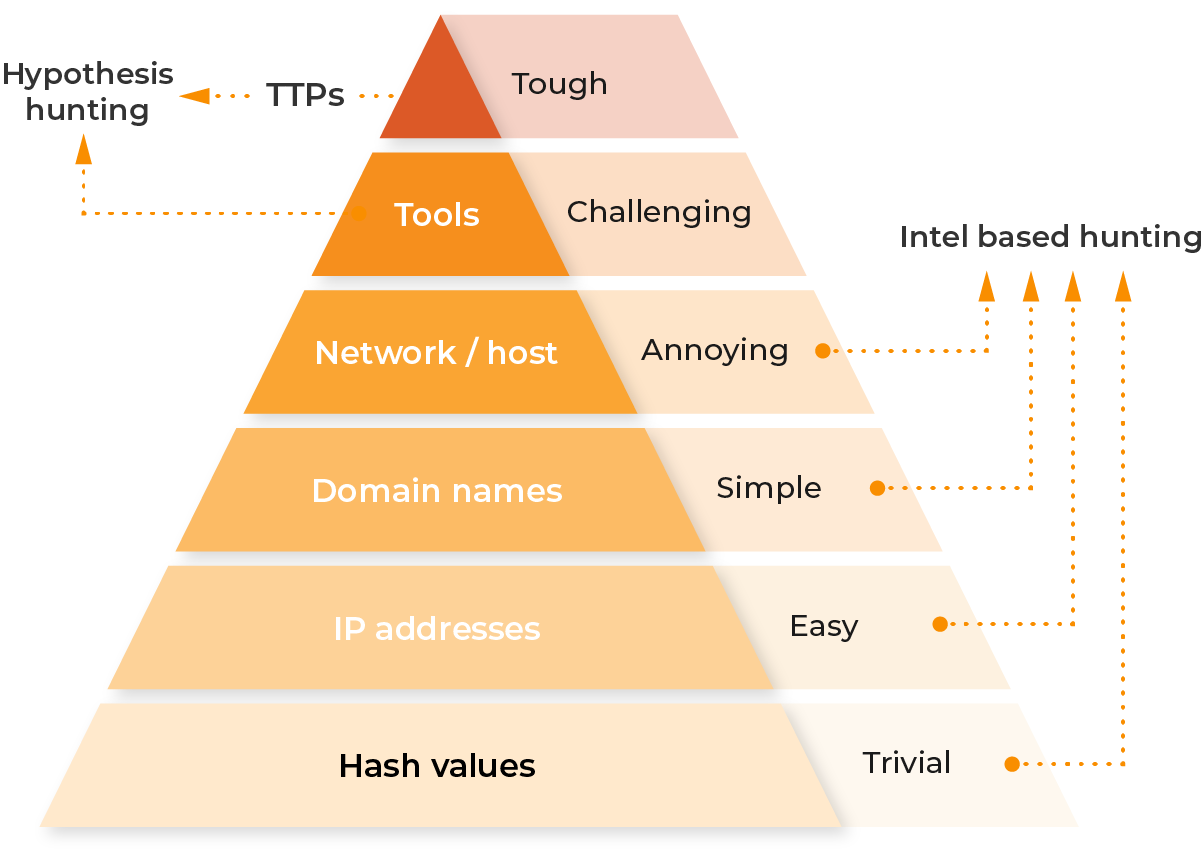
Lumu helps you build your way up the pyramid of pain, making it harder for adversaries to bypass your defense strategy.
MITRE matrix mapping builds a hypothesis showing techniques threat actors are using to target your organization.
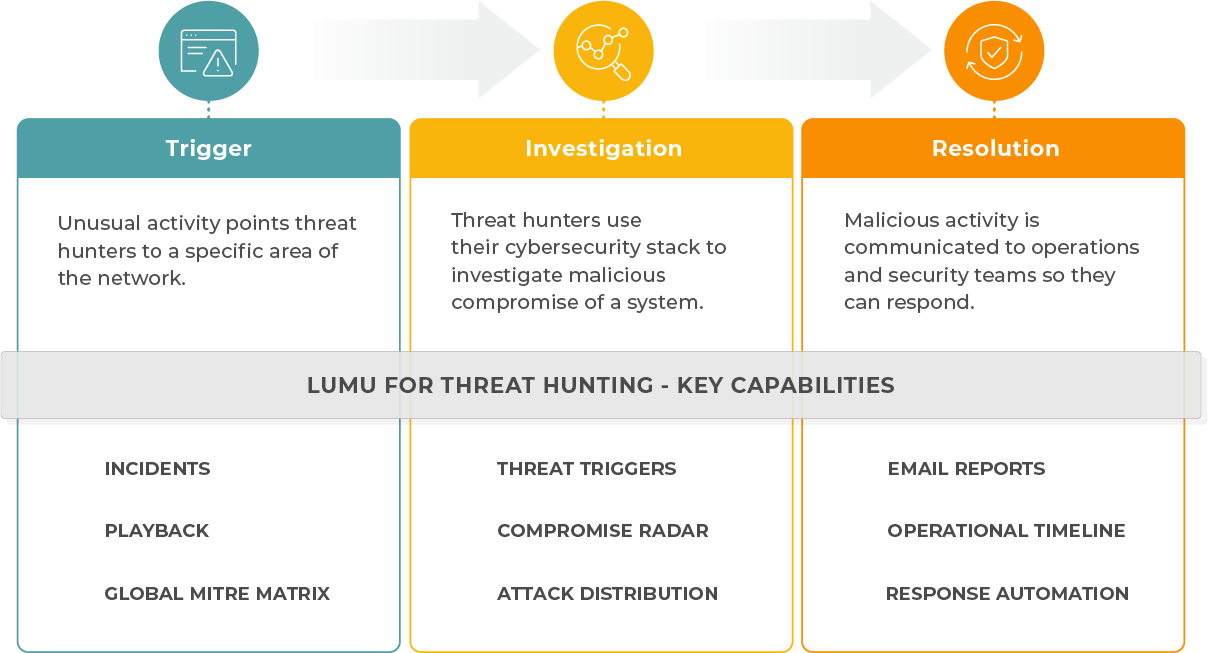
Incidents contain information that shows the attack type, and assets that have been potentially impacted.
Threat triggers provide threat hunters with all of the details needed to conduct an investigation.
Purpose-built threat detection model that aligns with your threat hunting practice
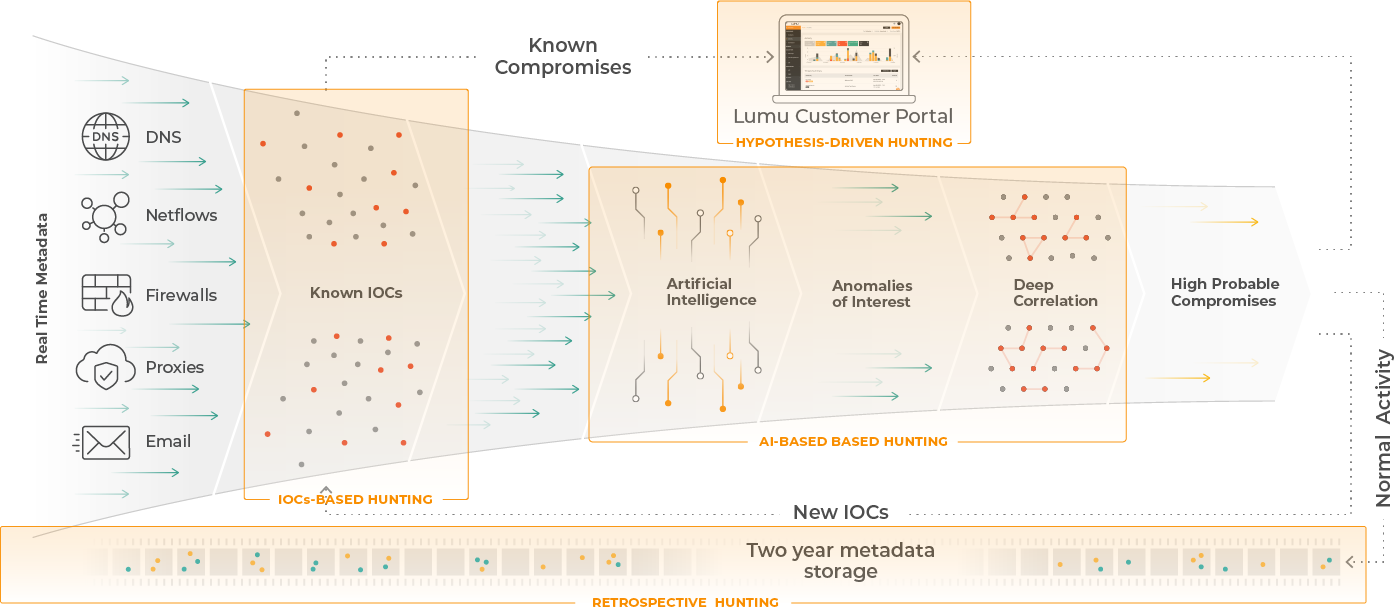
Lumu automates IOC-based threat hunting and streamlines curation of threat intelligence.
AI and ML detect behavioral anomalies to initiate threat hunting exercises.
2-year automated retrospective threat hunting with updated threat intelligence.
Automated MITRE mapping empowers sophisticated threat hunting hypotheses.
Lumu’s features are thoughtfully designed to help you each step of the way.
Provides coordinates and information from endpoints to trigger your threat hunting exercise.
Lumu stores 2 years of metadata to defend against zero-day threats and emerging attacks. This triggers a retrospective threat hunting exercise.
Provides details around how attackers are targeting your organization to prioritize threat hunting and red team exercises.
Contains IoCs related to an incident as reported by Lumu’s threat intelligence engines or third party sources.
Shows threat hunters contact patterns to help distinguish occasional contact from persistent and automated attacks.
Enables prioritization by uncovering which areas of the organization are most affected by threat actors.
Email all of the details of an incident and what actions were taken directly to your CISO and others as needed.
All incidents contain a timeline section where teams can track the steps of the resolution flow.
Connect Lumu with your existing cyber stack to take automated actions against active threats.
© Lumu Technologies All rights reserved. | Legal information.