MSSP Security Must Adapt to Serve Customers
Many businesses today cannot keep up with the ever-increasing volume and innovation of cyber threats and attackers. Honestly, they should not have to do so. This is why Managed Security Service Providers (MSSPs) have emerged as key players in the cybersecurity industry. MSSPs provide businesses with expert security services and technology stack to best defend those who cannot defend themselves. However, MSSP security stacks need to adapt to continue delivering quality services at scale.
What Drives MSSP Growth?
Managed Security Service Providers (MSSPs) are third-party organizations that offer a range of security services to businesses, such as threat monitoring, incident response, vulnerability management, and more. MSSPs operate as an extension of an organization’s internal security team or, in many cases, as a fully outsourced security solution. They employ a combination of advanced technologies, experienced professionals, and best practices to protect their clients’ networks, systems, and data from cyber threats.
Since 2021 there have been several factors that are driving the growth of MSSPs:
- Escalating Cyber Threats: The proliferation of cyber threats, including ransomware attacks, data breaches, and phishing attempts, has made cybersecurity a top concern for organizations across industries. The increasing frequency and sophistication of these attacks have compelled businesses to seek specialized expertise and advanced security measures, leading to the growth of MSSPs.
- Skills Gap and Resource Constraints: Building an in-house security team capable of combating modern cyber threats requires a significant investment in skilled professionals, training, and advanced tools. Many organizations struggle to attract and retain cybersecurity talent due to the high demand and competitive landscape. By partnering with MSSPs, businesses can leverage the expertise of experienced security professionals without the burden of hiring, training, and managing an entire team.
- Compliance and Regulatory Requirements: In an era of stringent data protection regulations, organizations must adhere to various compliance frameworks and industry-specific mandates. MSSPs assist businesses in meeting these requirements by implementing and managing security controls, conducting audits, and providing the necessary documentation to demonstrate compliance, thereby alleviating the compliance burden from internal teams.
- Cost-effectiveness and Scalability: Engaging an MSSP often proves to be more cost-effective than building an in-house security infrastructure from scratch. MSSPs offer flexible pricing models, allowing organizations to pay for the services they need, avoiding high upfront costs. Additionally, MSSPs can scale their services according to an organization’s evolving security needs, ensuring a tailored approach that aligns with the organization’s growth and changing threat landscape.
The Benefits of Partnering with an MSSP
Creating and managing an in-house cybersecurity program can be an overwhelming task, particularly for businesses without extensive resources or expertise in this domain. This is where Managed Security Service Providers (MSSPs) come into play. There are specific and quantifiable benefits to partnering with MSSPs rather than operating cybersecurity in-house.
- Proactive Threat Detection and Response: MSSPs employ advanced monitoring and analysis tools, leveraging real-time threat intelligence, and proactive security measures to detect and respond to potential threats before they cause significant damage. Their expertise in threat detection and response enables rapid incident resolution, minimizing downtime and reducing the impact of security breaches.
- 24/7 Security Operations Center (SOC): MSSPs typically operate dedicated Security Operations Centers staffed by experienced analysts who continuously monitor security events, investigate suspicious activities, and respond to incidents promptly. This round-the-clock surveillance ensures constant protection and provides organizations with peace of mind, knowing that their systems are being monitored and defended even outside regular working hours.
- Access to Cutting-edge Technologies: MSSPs have access to a wide array of state-of-the-art cybersecurity technologies and tools that may be costly for individual organizations to acquire and maintain. By partnering with an MSSP, businesses gain access to these advanced solutions, benefiting from the latest innovations and defenses against emerging threats.
- Focus on Core Competencies: Outsourcing security responsibilities to an MSSP allows organizations to concentrate on their core business functions, knowing that their security needs are in capable hands.
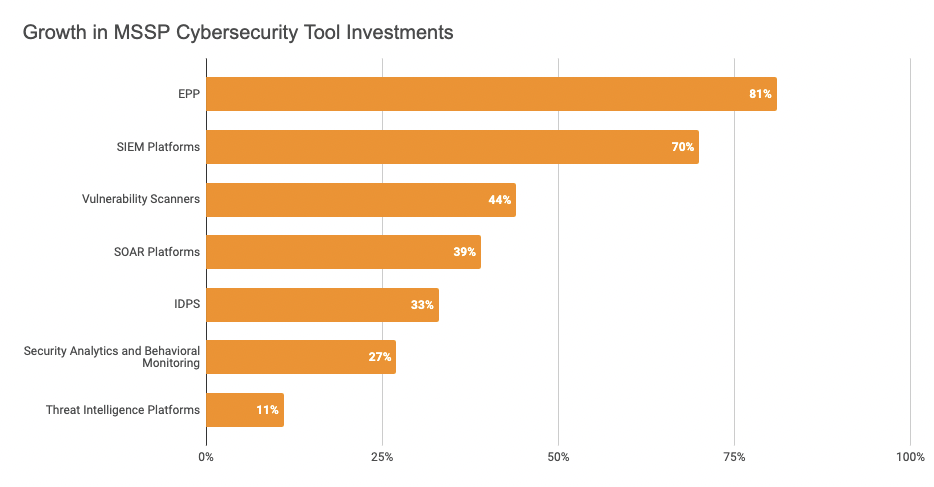
MSSP Security Stack Growth
Managed Security Service Providers (MSSPs) employ a variety of tools and technologies to help their customers to enable a total security stack. By analyzing the growth in the adoption of tooling in the MSSP security market we see that there are trends indicative of a general focus area and acquisition need:
- 70% investment in Security Information and Event Management (SIEM) Platforms: SIEM platforms aggregate and analyze data from various sources, including network devices, servers, and security appliances, to provide real-time visibility into security events. These tools enable MSSPs to detect and respond to threats by correlating and analyzing security data from across the network infrastructure. Despite SIEMs’ poor track record in detecting and responding to threats precisely or quickly, MSSPs continue to deploy SIEMs at the core of their cybersecurity operations.
- 33% investment in Intrusion Detection and Prevention Systems (IDPS): IDPS tools help MSSPs monitor network traffic and identify potentially malicious activities. These systems can detect and prevent attacks by analyzing network packets, monitoring for patterns that match known attack signatures or anomalous behavior, and taking proactive measures to block or mitigate threats.
- 44% investment in Vulnerability Scanners: Vulnerability scanners identify potential weaknesses in networks, systems, and applications. MSSPs utilize these tools to conduct regular vulnerability assessments and identify security gaps that could be exploited by attackers. By performing ongoing scans and assessments, MSSPs can proactively address vulnerabilities and provide recommendations for remediation.
- 39% investment in Security Orchestration, Automation, and Response (SOAR) Platforms: SOAR platforms enable MSSPs to streamline and automate their incident response processes. These tools integrate with various security technologies, centralize security alerts, and automate response actions, resulting in improved efficiency and faster incident resolution.
- 11% growth in Threat Intelligence Platforms: Threat intelligence platforms collect, analyze, and distribute information about emerging threats and the tactics, techniques, and procedures (TTPs) used by threat actors. MSSPs utilize these platforms to stay updated on the latest threats and incorporate this intelligence into their security monitoring, and incident response processes.
- 27% growth in the adoption of Security Analytics and Behavioral Monitoring: MSSPs leverage advanced analytics tools to detect anomalous behavior and potential indicators of compromise within their customers’ networks. By analyzing patterns and trends in network traffic, user behavior, and system logs, these tools can identify suspicious activities and flag potential security incidents.
Where MSSP Cybersecurity Services Are Heading
Within those adoption trends there are indicators of the “most valuable” MSSP security solutions. Because of the growing adoption of SIEM and SOAR: SIEM platforms and SOAR solutions have gained significant traction among MSSPs by nearly a factor of three over other solutions. According to a report by MarketsandMarkets, the SIEM market is expected to reach a value of USD 6.93 billion by 2025, indicating the increasing demand for these tools as MSSPs and enterprises have been the primary buyers.
While MSSPs possess a wealth of expertise and advanced tooling, they’re still exposed to pitfalls. Here are some potential limitations or considerations when it comes to potential gaps in MSSP security stacks due to their reliance on tooling and point solutions:
- Lack of Context and Understanding: MSSPs typically work with multiple clients and handle diverse security environments. Due to this broad focus, they may not have an in-depth understanding of an organization’s specific business processes, critical assets, or risk appetite. This can potentially lead to generic or less-tailored security solutions that might not fully align with an organization’s unique needs.
- Limited Visibility and Control: When organizations outsource their security functions to an MSSP, they inherently relinquish some degree of control over their security operations. While MSSPs provide monitoring and reporting capabilities, there may be limitations on visibility into the inner workings of the security infrastructure, access to raw data, or the ability to make real-time changes to security configurations. Organizations must carefully evaluate the level of control they require and ensure it aligns with the MSSP’s capabilities. As all attacks have to use the network to achieve threat actors’ ends, the network is the ultimate source of truth to discover threat actors’ presence and actions. Picking up on threat actors’ ‘breadcrumbs’ is key to being able to respond to compromises quickly and effectively.
- Communication and Responsiveness: Effective communication and prompt response are vital in the event of a security incident. However, the response time and effectiveness of an MSSP can vary depending on factors such as their workload, availability of resources, and the severity of the incident. It is crucial to establish clear communication channels and define expectations regarding incident response to ensure a timely and efficient resolution.
- Dependency on Third-Party Relationships: MSSPs often rely on partnerships with third-party vendors for various security technologies and tools. While these partnerships enable MSSPs to offer a wide range of services, they also introduce an element of dependency on the reliability, performance, and security of these vendors. Any weaknesses or vulnerabilities in the third-party solutions can potentially impact the overall security posture provided by the MSSP.
- Complexity of Integration: Integrating an MSSP’s services with existing security systems and workflows can be challenging. Organizations may need to invest time and resources in establishing seamless integration, ensuring that data flows smoothly, and avoiding conflicts or duplications with existing security measures. Proper planning and coordination are crucial to avoid potential disruptions or gaps in security coverage during the integration process.
- Compliance and Regulatory Considerations: Organizations that operate in highly regulated industries or geographies may face additional challenges when working with MSSPs. Ensuring compliance with specific regulations, managing data sovereignty concerns, and meeting audit requirements might require careful evaluation and clarification of responsibilities between the organization and the MSSP.
So what is the takeaway in all of this data and discussion? It’s pretty simple. Most businesses can and will benefit from partnering with an MSSP. If you cannot “do” security completely, work with someone that can and does. One cannot be part of the way in on a security need and expect things to work. However, there are potential risks and gaps in many MSSP coverages and offerings that customers should be aware of.
The trends and data indicate that MSSPs are buying technology just as fast and as haphazardly as the average buyer. This leads to confusion, loss of context, and the risk of missing a valid security incident. Be sure that your MSSP can operate with total context and full functional cognizance of and visibility into your network infrastructure. And be sure they have a means of remediating a threat as efficiently as possible. Seeing a problem and not being able to fix it is not what you are paying for.
Lumu for MSPs/MSSPs helps Managed Security Service Providers to ensure that every element of their security stack provides value alongside an integrated security ecosystem. Learn more about Lumu for MSPs/MSSPs.



