Table of Contents
What Is CIS?
The Center for Internet Security (CIS) is a nonprofit organization dedicated to improving cyber defense by creating and promoting best practices. They collaborate with cybersecurity and IT experts from government, business, and academia worldwide to develop their standards. These guidelines are established through a consensus-driven process, ensuring they reflect the collective expertise and experience of the global cybersecurity community.
The CIS provides a set of globally recognized best practices known as CIS Controls, designed to enhance cybersecurity by mitigating common threats. These controls are categorized into basic, foundational, and organizational groups, which help organizations improve their security posture through prioritized and actionable guidance. Compliance with CIS simplifies regulatory compliance, enhances risk management, and optimizes resource allocation.
The Importance of CIS Compliance for MSPs
As cyber threats escalate, businesses increasingly rely on MSPs for IT support and cybersecurity needs. However, this reliance also heightens the risk of cyber-attacks, as MSPs become attractive targets due to their access to multiple clients’ systems. Cybercriminals frequently target MSPs, over the last two years, ransomware attacks against MSPs have risen approximately 94%.
The CIS framework, with its straightforward language and 18 high-priority best practice categories, is accessible and crucial for developing a formalized security program. By following CIS guidelines and leveraging security automation, MSPs can simplify the management of cybersecurity risks and protect their clients’ data and systems.
Mapping Lumu to CIS Controls
There is no single technology that will check all 18 CIS controls, however, Lumu helps MSPs check some of these critical requirements through its extensive visibility and automated response capabilities. Below we’ve highlighted where Lumu’s capabilities enable full compliance with CIS controls. All are mapped as follows:
Control 10: Malware Defenses
Control Requirement – Prevent or control the installation, spread, and execution of malicious applications, code, or scripts on enterprise assets.
Lumu’s Approach – Lumu detects malware related incidents on any device and automatically reports and blocks different types of malware and precursor ransomware in real-time. All details around endpoints affected and the behavior of a particular instance of malware can be found in the incident details.
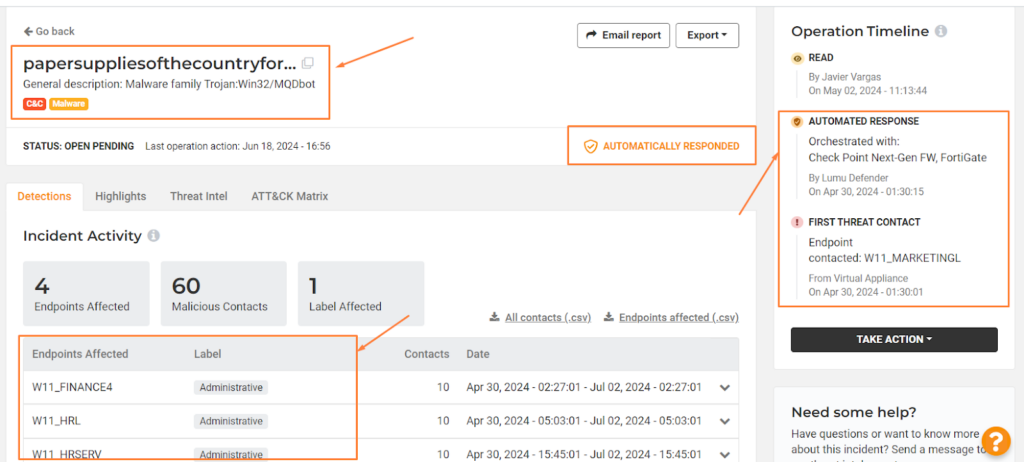
Control 13: Network Monitoring and Defense
Control Requirement – Operate processes and tooling to establish and maintain comprehensive network monitoring and defense against security threats across the enterprise’s network infrastructure and user base.
Lumu’s Approach – Lumu works 24x7x365 monitoring the entire network for any unusual activity. Taking every aspect of the network into account, Lumu is able to investigate unusual activity to identify active threats and stop them in real-time using existing perimeter defenses and endpoint tools. All activity is tracked and reported in detail. Incidents discovered by Lumu may also be sent to existing SecOps and PSA tools for further investigation.
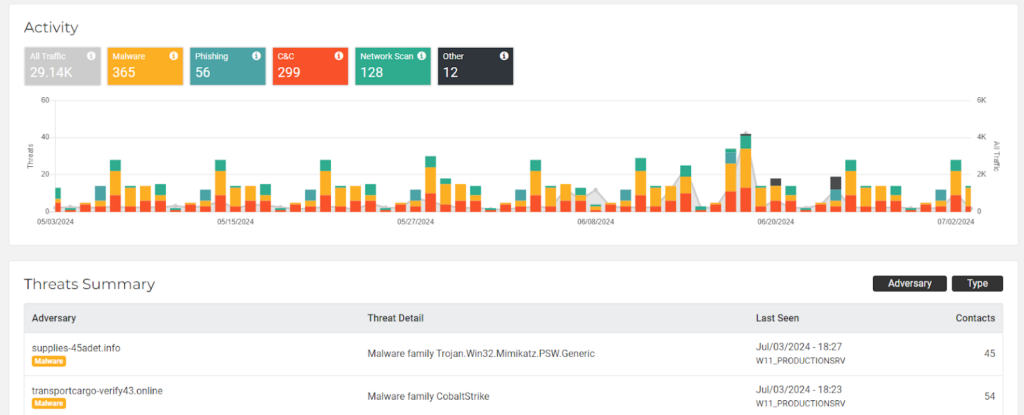
Control 17: Incident Response and Management
Control Requirement – Establish a program to develop and maintain an incident response capability (e.g., policies, plans, procedures, defined roles, training, and communications) to prepare, detect, and quickly respond to an attack.
Lumu’s Approach – With hundreds of product integrations available, Lumu responds to incidents in real-time, without the need for human intervention. Once a threat is detected, actions are automatically taken to stop the adversary before any damage occurs. All incidents can be managed within the Lumu portal.
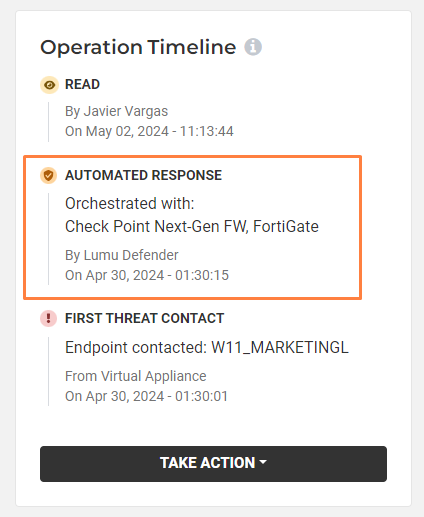
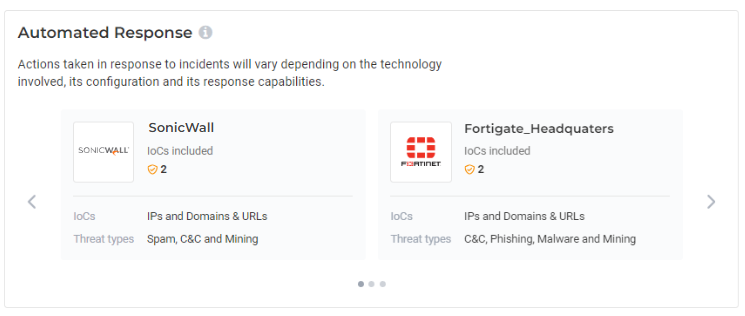
Get Started with Lumu
Though being fully compliant with CIS may seem like a daunting task, the best approach is to handle it a few steps at a time. Lumu offers a free solution for MSPs including up to 3 tenants, with 3 integrations (including integrations for data collection, response, and security operations), and up to 50 endpoints. To learn more about how Lumu can help achieve compliance with CIS access our CIS Enablement Document here.



