Table of Contents
Defending small to medium-sized enterprises from cyber threats is now an established part of the role of an MSP. Standing on the frontline against cybercriminals, it is essential for MSPs to gather cyber threat intelligence and to use it well.
In the Lumu Compromise Report 2024, it was revealed that a substantial percentage of cyber attacks targeted IT and services, a large percentage of that category being MSPs. In other words, cyber criminals are not only after MSP clients but MSPs themselves.
Let’s look at how to use cyber threat intelligence to ensure a robust threat-informed defense that maintains both MSPs and their clients are safe from cyber attacks.
If you know the enemy and know yourself, you need not fear the result of a hundred battles.
Sun Tzu, The Art of War
Tip 1: Know The Enemy
The world of cybersecurity moves quickly, and — as we can see in this report — threat actors come and go and their techniques diverge and change. This means that MSPs must keep their ear to the ground and make sure that they are up to date with the most recent threat intelligence.
Much of this intelligence is about getting to know the enemy. Knowledge about where cybercriminals are attacking and which methods they are using to attack will help guide our defensive postures and strategies. The latest strategic intelligence is essential to understand the threat horizon and helps plan ahead — which is why Lumu develops an annual Compromise Report to share our insights with our customers and partners.
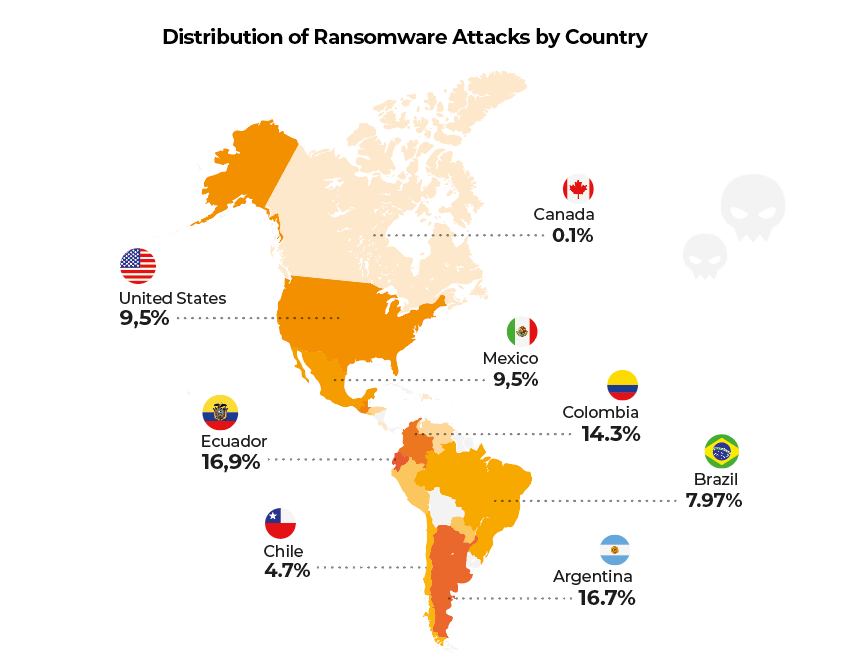
Lumu Sheds Light on the Cyber Enemy
The Lumu Compromise Report 2024 gives up-to-date information on the top malware tools being discovered. It also sheds light on into the specific families of malware that are being detected and where they are coming from.
Since Lumu uses the network as the primary source of information gathering, this means that the threats recorded are often bypassing traditional defenses, such as EDRs or firewalls.
Lumu’s report also highlights the sectors and industries, and the specific countries that are being targeted. These trends often reveal patterns, such as in which sectors malware is finding its way past defenses most effectively, or which countries are being targeted by certain groups.
Remember, however, that knowing your enemy is only part of Sun Tzu’s advice (and threat informed defense). One must also know oneself.
Tip 2: Know Yourself
Small and medium-sized enterprises might not have the budget to develop their own cyberdefense. This means that they rely on MSPs to keep their systems and their data safe.
MSPs need to understand their clients’ networks, security stacks, and find any weak spots. This is where intelligence from network visibility gives a huge advantage.
Not only this, but MSPs themselves are increasingly in the crosshairs. Cybercriminals have seen financial and tactical advantage in targeting MSPs as IT services hold large amounts of information and credentials, both on themselves and their clients.
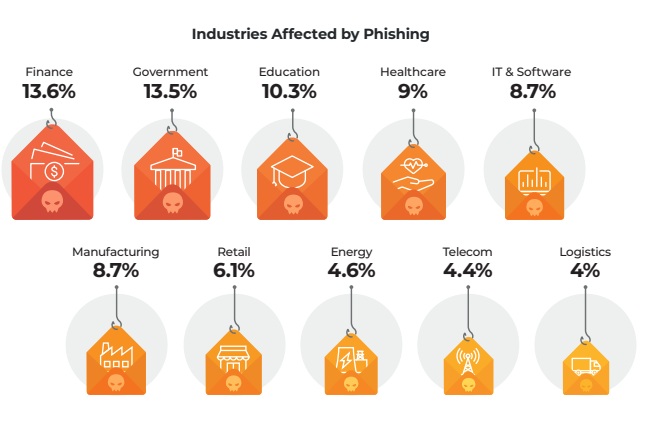
The Lumu Compromise Report 2024 recorded 8.7% of phishing attacks as targeting IT and software.
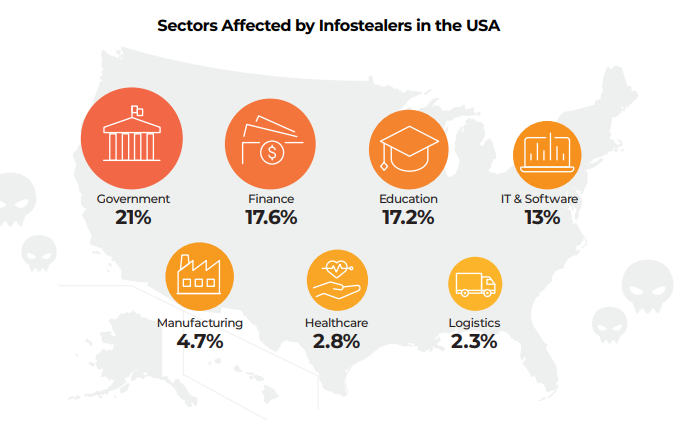
Infostealer attacks in the USA also had IT as a major target, at fourth, with 13% of all attacks.
Perhaps the statistic that will make most MSPs sit up and pay attention is that IT was the third sector affected by Ransomware, with 15.1% of the attacks.
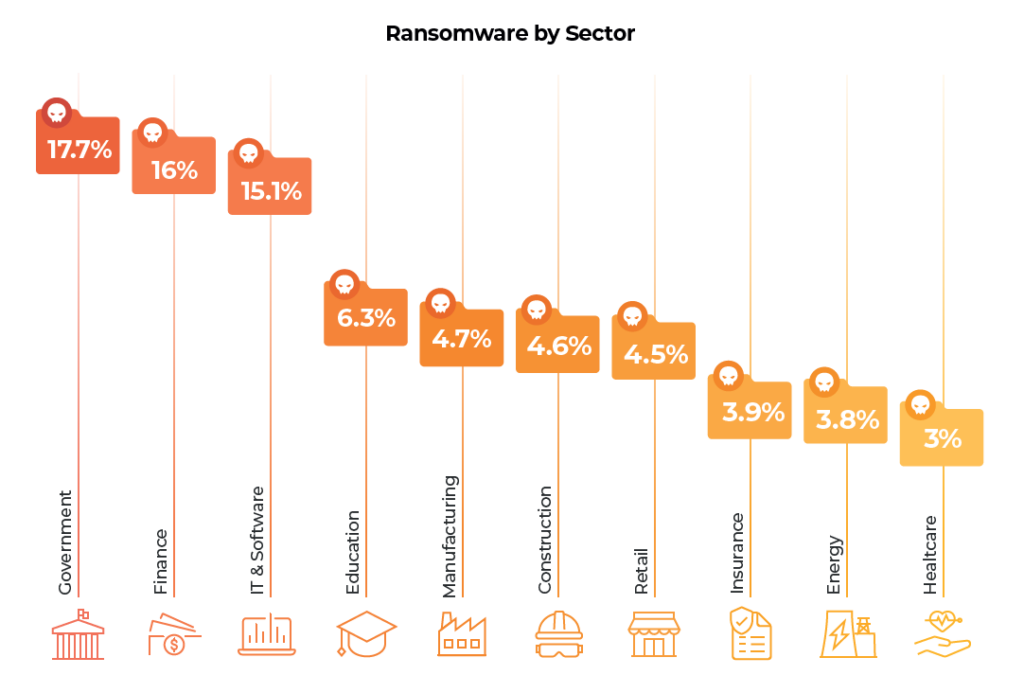
It’s worth noting that this data is taken separately from the attacks on our MSP partners’ clients, who come from a variety of sectors, meaning that once they are included the cases being dealt with by MSPs is brought up to a much larger percentage of the cases recorded.
Use the Matrix
The Lumu Compromise Report 2024 also reveals how Lumu is currently helping its partners to understand the intelligence landscape to develop their defenses.
MITRE is a good source of tactical intelligence that can be used to help defend against attacks. The report dives into the ten most common MITRE ATT&CK® techniques that have been recorded.
It also touches on how the Lumu Portal offers the Global MITRE ATT&CK Matrix®, which gives intelligence specific to one organization, allowing MSP SecOps teams to adjust their cybersecurity posture according to the threats and techniques that each organization is facing most often.
Another important factor in a threat-informed defense is keeping logs in order to effectively review activities. Lumu’s new feature makes logs available to MSPs, which will help forensic investigations into breaches and ensure that no rocks are left unturned.
This internal intelligence gathering works in unison with the big-picture strategic intelligence to guide MSPs to ensure that both them and their clients remain well-protected against cyber threats.
The Greatest Victory
As Sun Tzu says,
The greatest victory is that which requires no battle.
Using the most recent intelligence helps build a strong threat-informed defense and adjust both methodology and cyber infrastructure in accordance with the real on-the-ground situation. This reduces the risk of a cyber attack being successful — giving victory without the need for a battle.
To find out more about the latest trends, and how to be proactive in protecting your clients against cyber threats, download the Lumu Compromise Report 2024 today.



